Hello, in this article, we will first see how to get a memory image from linux systems and how we can analyze them. Many of the systems used today use the Windows operating system. Of course, forensic analysts are more knowledgeable on windows systems, but the use of linux operating systems is also not to be underestimated.For this reason, I wanted to start such a series. The memory image contains many sources of information for analysts during forensic analysis. Getting a memory image for Windows systems is child’s play, and when we switch to a linux operating system, things get a little complicated.
Well, let’s start slowly. First of all, it was easier to get the memory image of older version linux systems. We could get the memory image of the system via "/dev/mem", but this is no longer possible in new versions. There are a few tools that you can use to get the image of the memory, and I will write them and I will show them how these things work on two of them.
FMEM
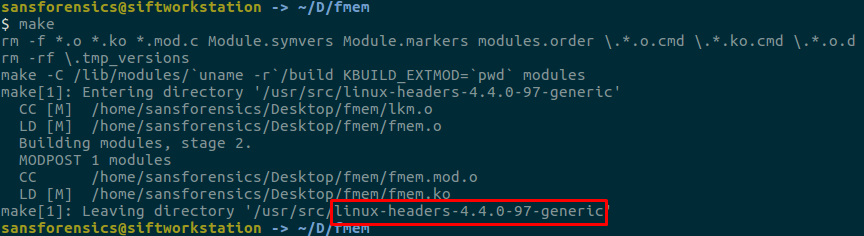
Let’s start with fmem first. You can get a memory image of a linux system using fmem. There is an important issue, of course, where fmem has to load its own small modules into the system, but it can be ignored for the evidence that can be obtained from this memory image. After downloading, you can make fmem ready to use by entering the following commands in the queue.
| |
Install this if you get an error. apt-get install dwarfdump
| |
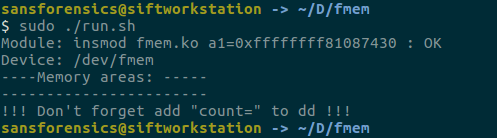
After installing fmem, you can get the memory image as follows using dd.
| |
Thus, we got the memory image of linux system on usb.
LiME
LiME is a command-line tool for acquiring various types of data for forensic purposes.
It also minimizes its interaction between user and kernel space processes during acquisition, which allows it to produce memory captures that are more forensically sound than those of other tools designed for Linux memory acquisition.
In order to use LiME, we have to load the modules into the system again. First of all, we need to go to the /LiME/src we downloaded and run the following.
| |
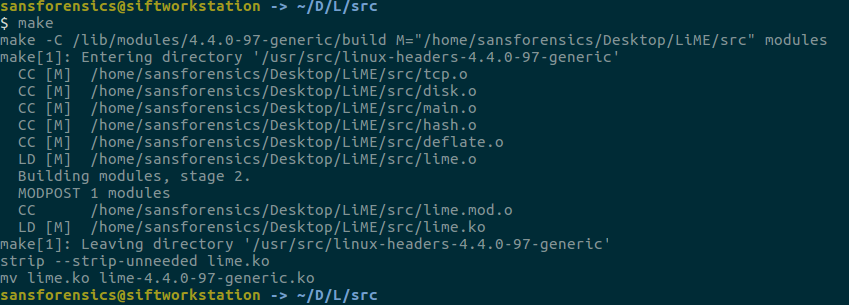
At the end of this process, it was compiled as a downloadable kernel object for the relevant linux version. We are now ready to receive the memory image. Now we will take the following actions. I want to print on a usb here so I gave the path of the usb memory. I have to remind you something here. Memory images are not small in size, so make sure there is enough space in the unit where you want to take the image.
| |
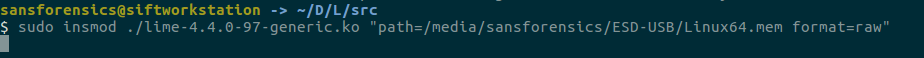
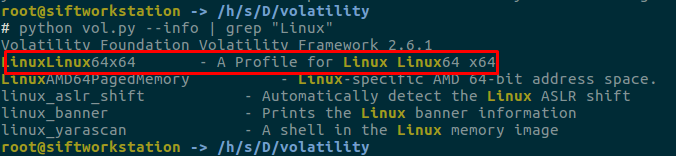
Well, we learned how to get images. We will use volatility in the analysis part, but here is a very important place, there are very few and limited numbers of linux profiles on volatility. If a profile file belonging to the system you have taken is not found on volatility, we need to create our own profile file.
Profile File Create
In the relevant version, the data structures of the kernel are created by going to the “tool/Linux” in the volatility directory and running the make command.
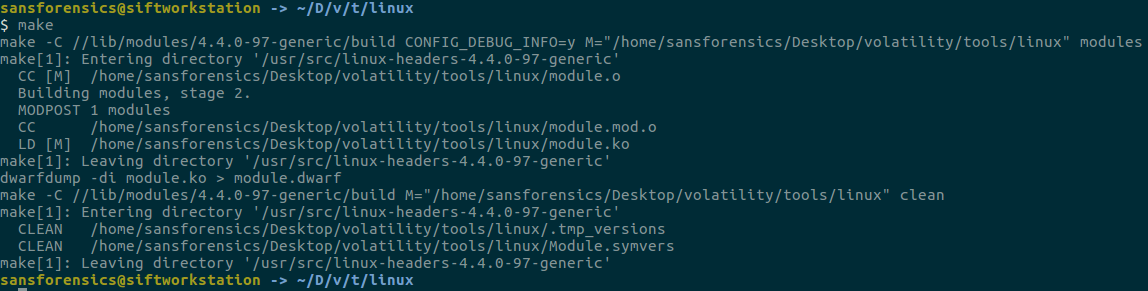
Then, another file we need will be the System.map file. You can find this file in the "/boot" directory in the respective operating system. Then we need to compress these two files with a zip application and copy them under “volatility/plugins/overlay /linux”
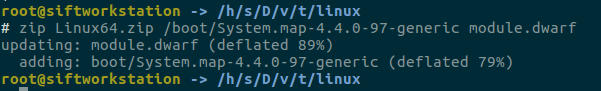
Let’s see our profile after copying it to the relevant directory?
| |