This article was prepared with the contribution of Adeo DFIR Team.
Hello to everyone. On August 9, Defcon DFIR CTF, provided by the Champlain College’s Digital Forensic Association, will be broadcast live. I did not have the opportunity to look at the first days of publication, and later I had time and we finished the 4th place.
Together with my friend, we are doing an internship at the DFIR department at ADEO IT Consulting Services and when we saw the competition we wanted to participate and write such a post.After completing the competition, we found that the degree of difficulty was very small, we expected a few different scenarios in this competition. I want them to make it more enjoyable with scenarios like Lateral movement detection next year.
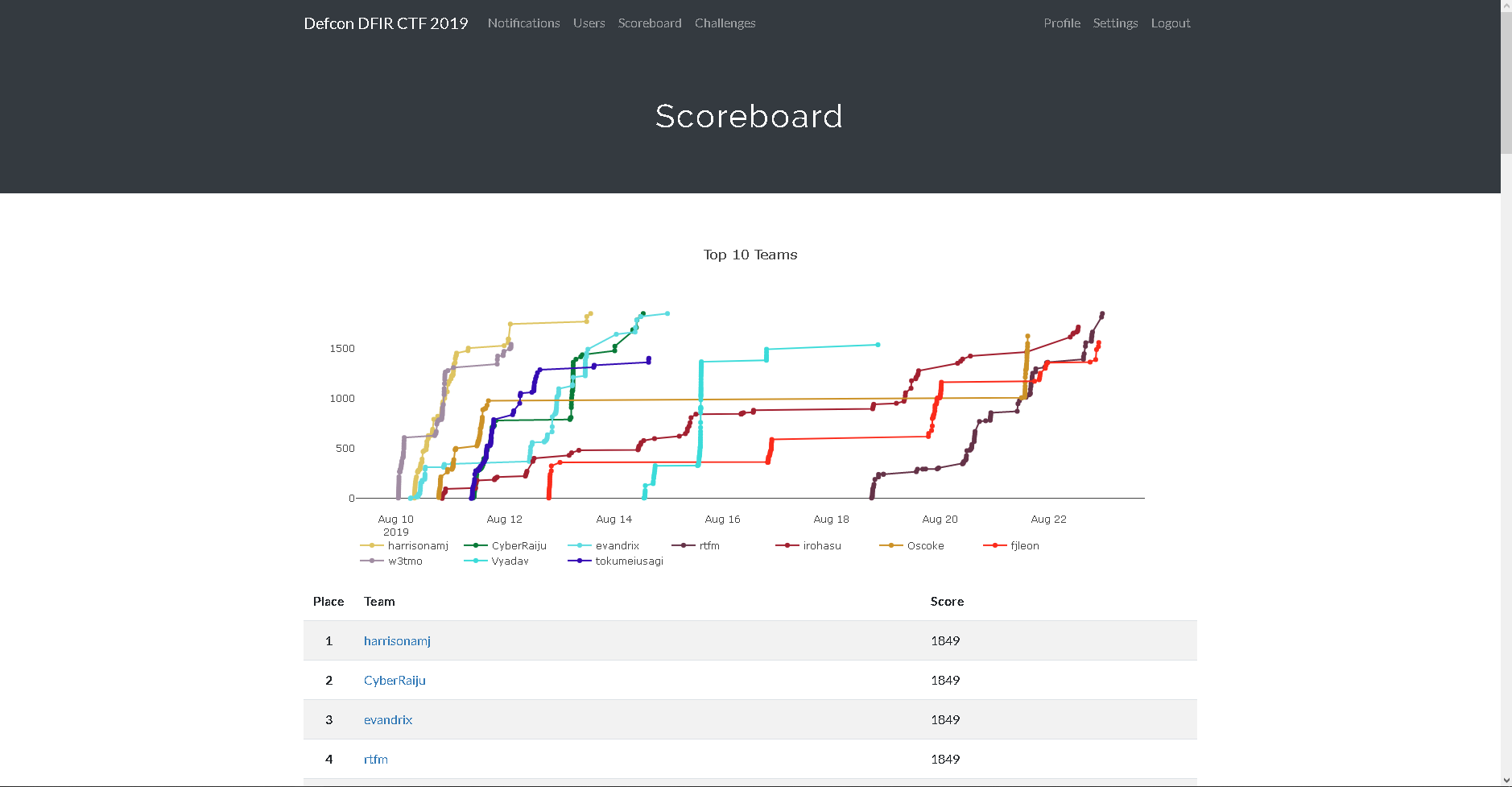
Defcon DFIR is comprised of 5 different categories with a total of 82 DFIR-related challenges including CTF, Crypto Challenge, Deadbox Forensics, Linux Forensics, Memory Forensics, and Live VM Triage. After solving all the questions we decided to write a writeup. The first article of the Writeup series will be Memory Forensics.
Memory Forensics#
get your volatility on (5 Point)#
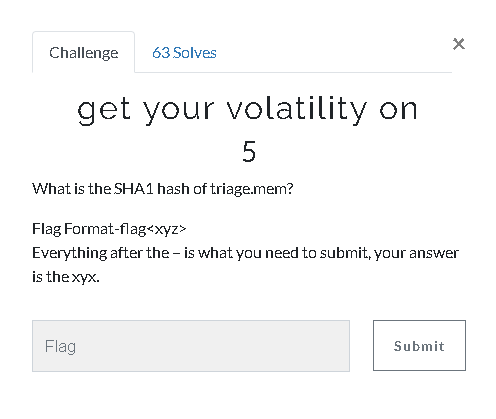
You can easily calculate the sha1 hash value of the downloaded memory image via Powershell, you can use “gi * .mem | filehash -Algorithm SHA1 " command.
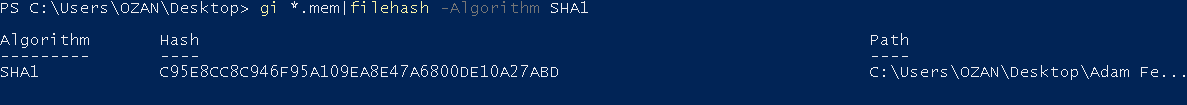
Or you can calculate the hash value by saying sha1sum on the bash shell.
1
| sha1sum Adam\ Ferrante\ -\ Triage-Memory.mem
|
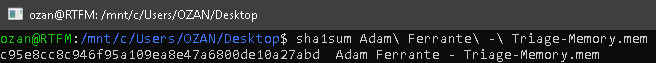
Flag< c95e8cc8c946f95a109ea8e47a6800de10a27abd>
pr0file (10 Point)#
Using Volatility in this question we can easily reach the right conclusion. Volatility will also list the possible profiles in the image with the “imageinfo” parameter.
1
| volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem imageinfo
|
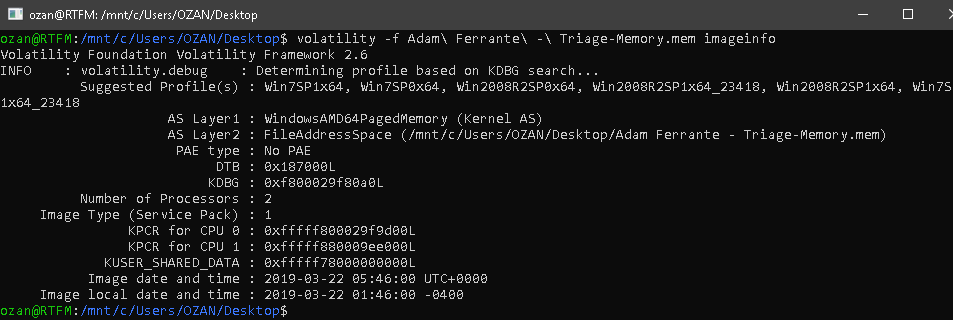
In general, the first of the matching profiles is the most appropriate. Instead, you can get the correct result by saying
1
| "volatility -f <image_file> kdbgscan" in volatility.
|
Flag< Win7SP1x64>
hey, write this down (12 Point)#
Volatility’s “psscan” or “pslist” module will handle this easily.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 psscan"
|
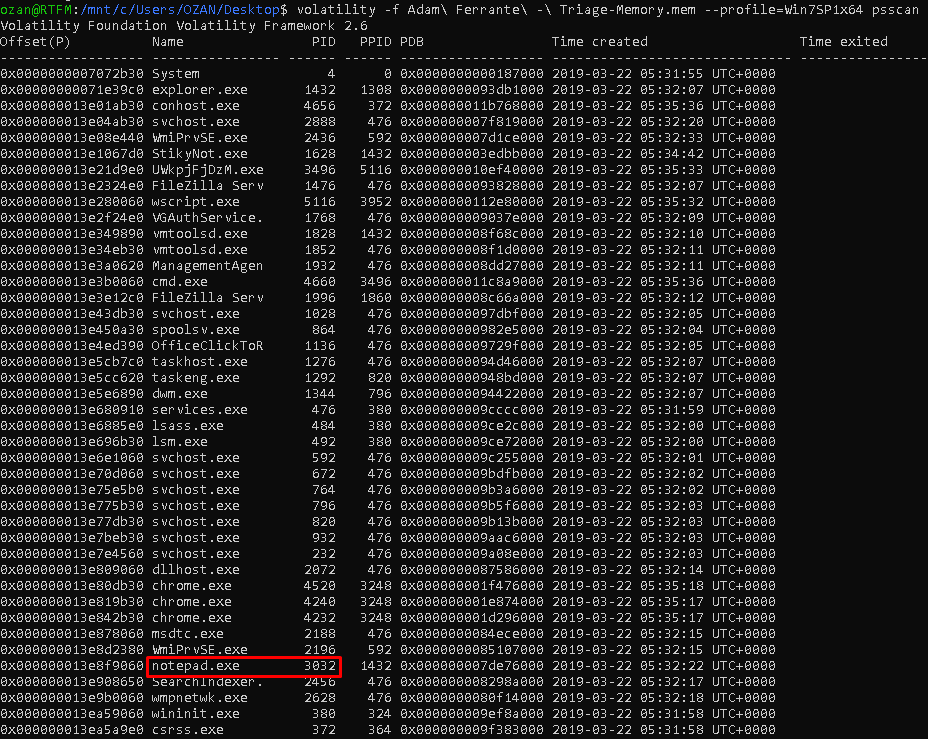
Flag<‘3032>
wscript can haz children (14 Point)#
This question can also be accessed from the previous question. By looking at the processes list, it can be determined that wscript.exe is running under wscript.exe, or the pstree module on volatility can be used to find out which procesess matches the ppid.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 pstree"
|
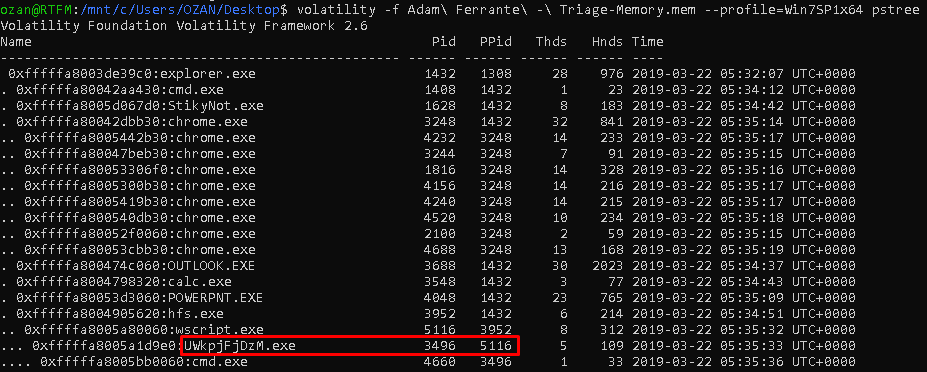
Flag< UWkpjFjDzM.exe>
tcpip settings (18 Point)#
Using the at “netscan” module in volatility, we can detect local threads.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 netscan"
|
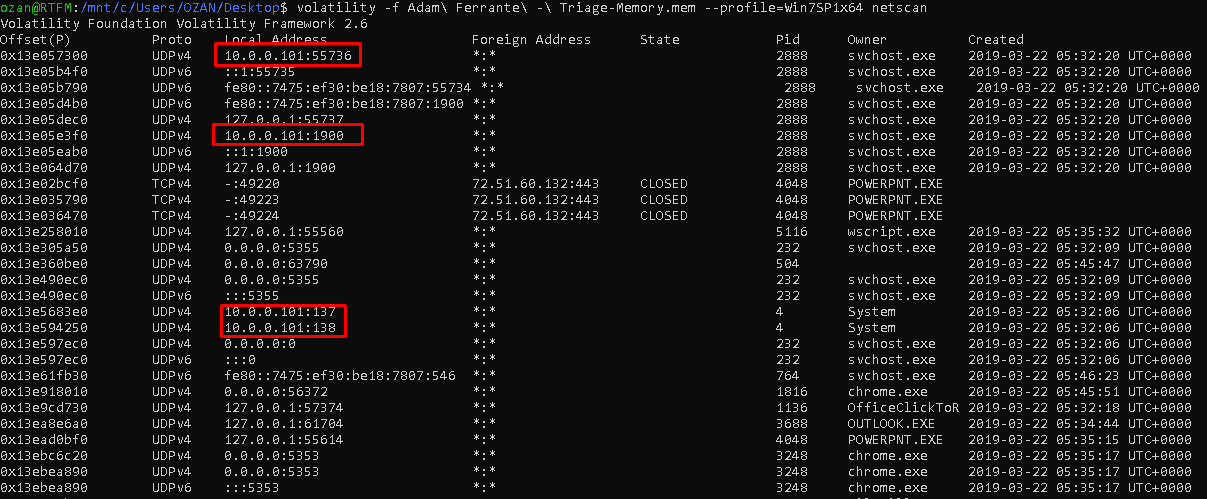
Flag<10.0.0.101>
intel (18 Point)#
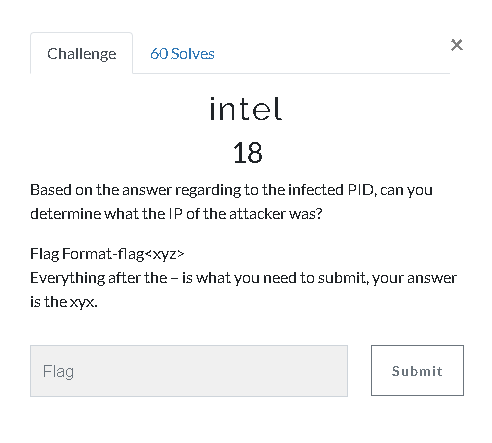
Here we understand that the file running under wscript.exe is actually a malicious, we know the name of the file, just look at the previous question screen a little enough.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 netscan"
|
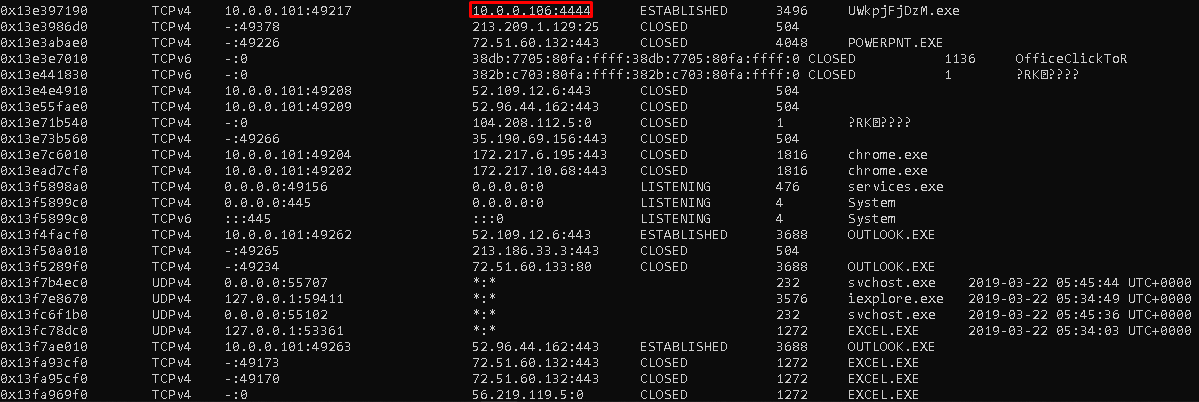
Flag<10.0.0.106>
windows dependencies (20 Point)#
On this question we only use the “dlllist” module of volatility and a few grep parameters.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 dlllist | grep "VCRUNTIME140.dll" -B 40"
|
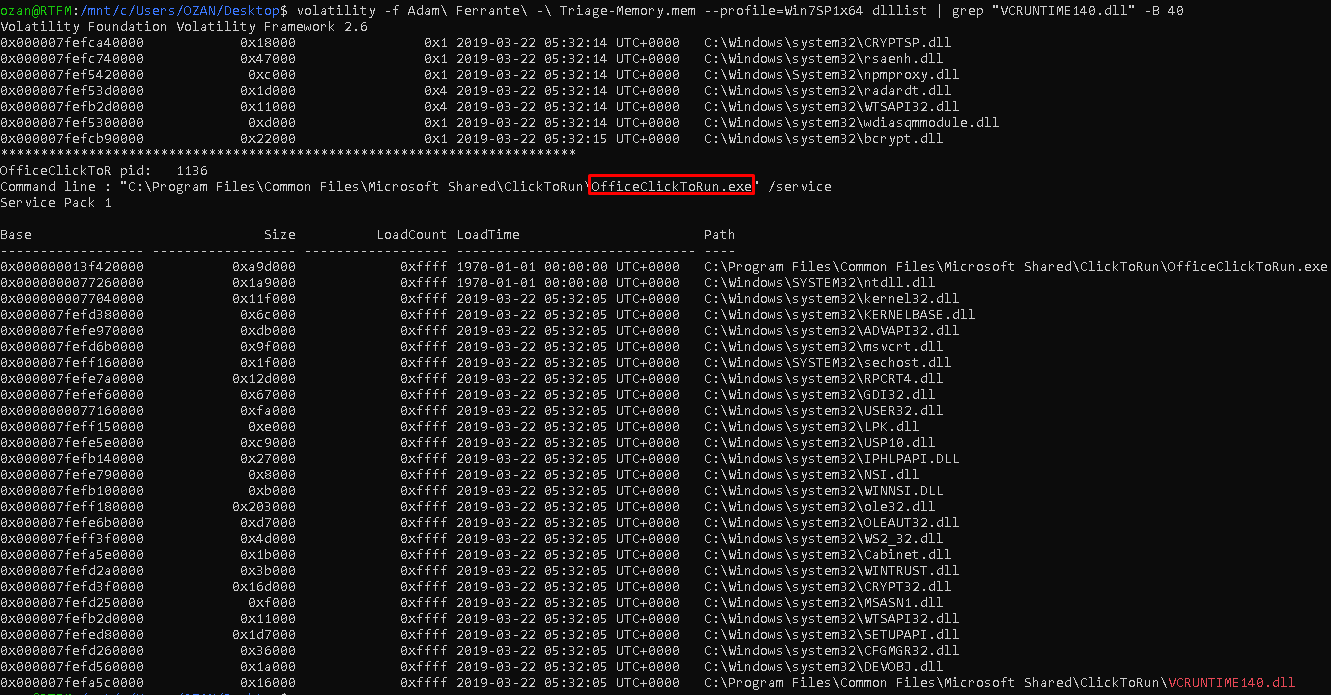
Flag< OfficeClickToRun>
mal-ware-are-you (20 Point)#
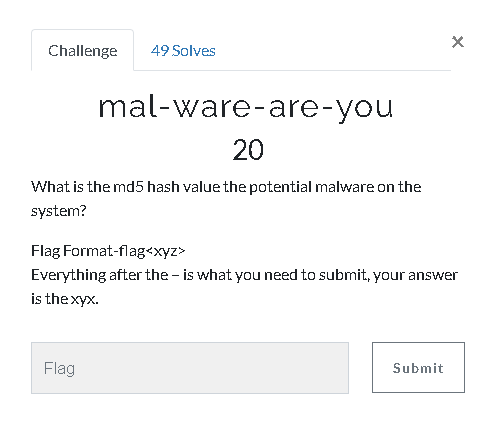
We know malware running on the system. So how do we calculate its md5 hash value? It is a module that enables us to obtain and examine process dumps (as it is in memory) thanks to the “procdump” module included in volatility. The commands we need to run for this are as follows:
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 procdump -p 3496 - dump-dir ./"
|
1
| "md5sum executable.3496.exe"
|
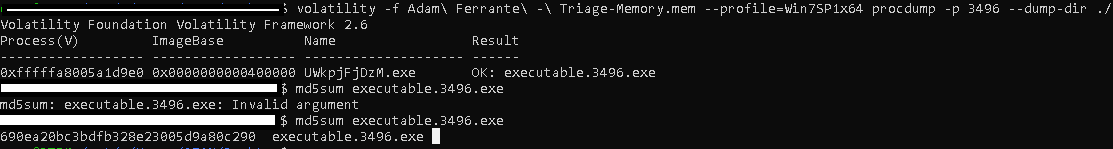
Flag< 690ea20bc3bdfb328e23005d9a80c290>
lm-get bobs hash (24 Point)#
If we have a full memory dump, volatility can be obtained by using the “hashdump” module. To do this, we first need to learn the virtual addresses of the “SYSTEM” and “SAM” hive files.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 hivelist"
|
1
2
|
"volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64" "hashdump -y 0xfffff8a000024010 -s 0xfffff8a000e66010 > hash.txt"
|
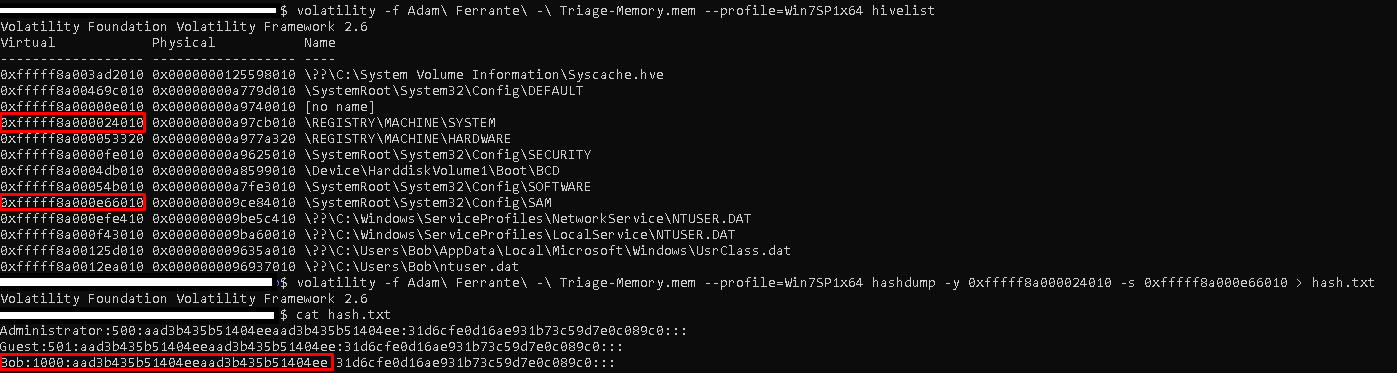
Flag< aad3b435b51404eeaad3b435b51404ee>
vad the impaler (25 Point)#
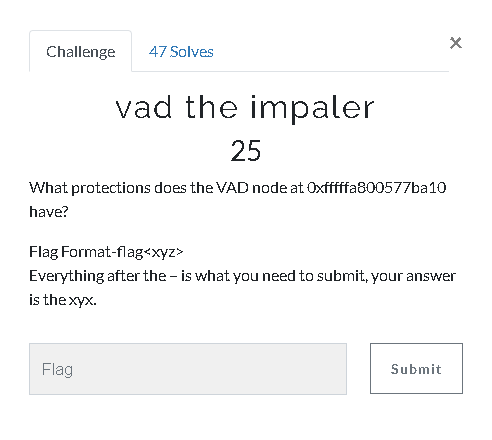
Volatility contained in “vadinfo” and “grep” can be found comfortable when used protection.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 vadinfo | grep " 0xfffffa800577ba10" -A 5"
|
Flag< PAGE_READONLY>
more vads?! (25 Point)#
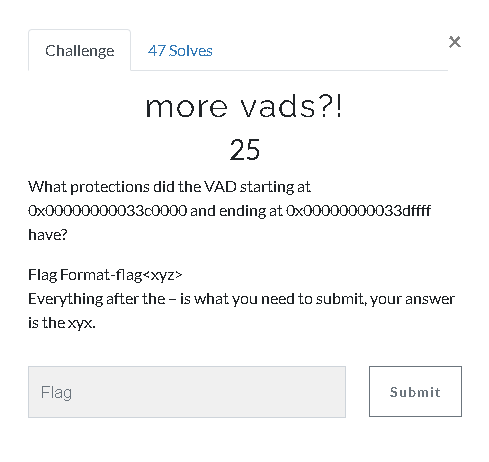
In the same way as the previous question, we will only need to make a small change to the grep.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64" "vadinfo | grep "Start 0x00000000033c0000 End 0x00000000033dffff" -A 5".
|
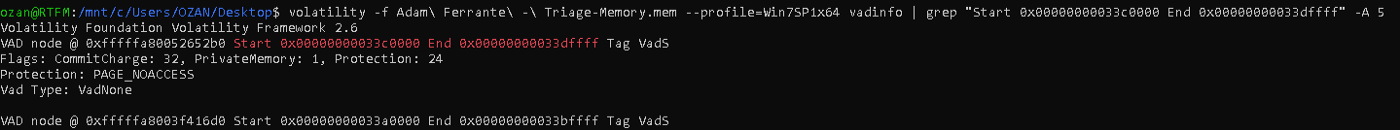
Flag< PAGE_NOACCESS>
vacation bible school (25 Point)#
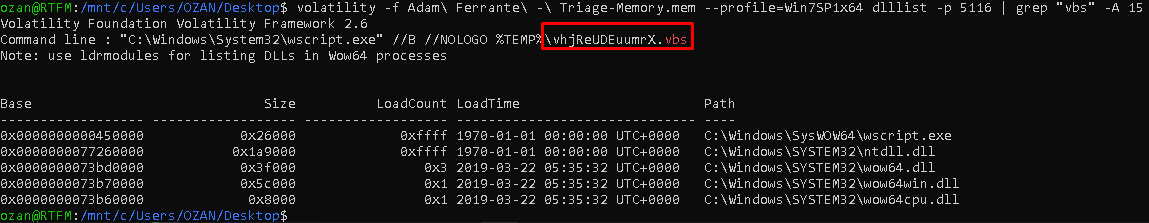
He asked us for the name of the “VBS” one script that worked on this question. For this question, the dump of wscript.exe can be retrieved, followed by a string with a file name, or by using “dlllist” and “grep” for wscript.exe.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 dlllist -p 5116 | grep "vbs" -A 15"
|
Flag
thx Microsoft (25 Point)#
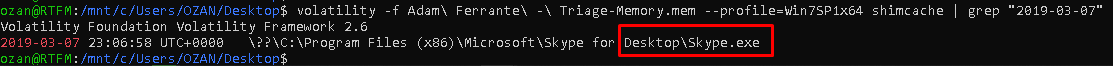
The program names, sizes, last run times etc. of the programs that are run in the “Shimcache” file in the Windows systems. data. If we parse this file using true “shimcache” module in Volatility and grep a certain date or time, we can get the right result.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 shimcache | grep "2019–03–07"
|
Flag<Skype.exe>
14.lightbulb moment (35 Point)#
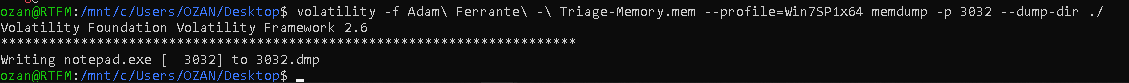
For this question, we first need to take the dump of notepad.exe and then look at the strings. To get dumped,
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 memdump -p 3032 - dump-dir ./"
|
After the dump process is finished, we reach a small search by saying flag in the strings.
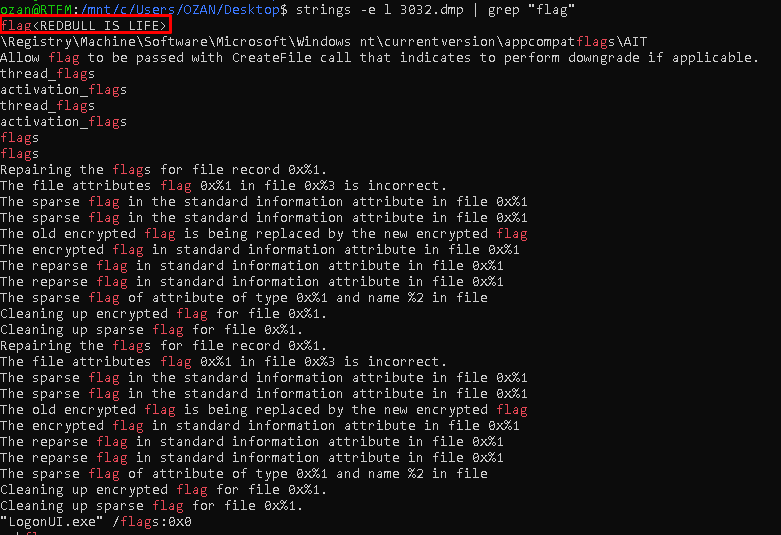
Flag<REDBULL_IS_LIFE>
15.8675309 (35 Point)#
Windows systems are something we can call the heart of the NTFS file system, that's MFT. Information about all files and directories in the system is stored in the MFT. This includes the record number. Thanks to the "mftparser" module in volatility, we can extract the file of the given mft registration number with grep.
1
| "volatility -f Adam\ Ferrante\ -\ Triage-Memory.mem - profile=Win7SP1x64 mftparser | grep "59045" -A 30"
|
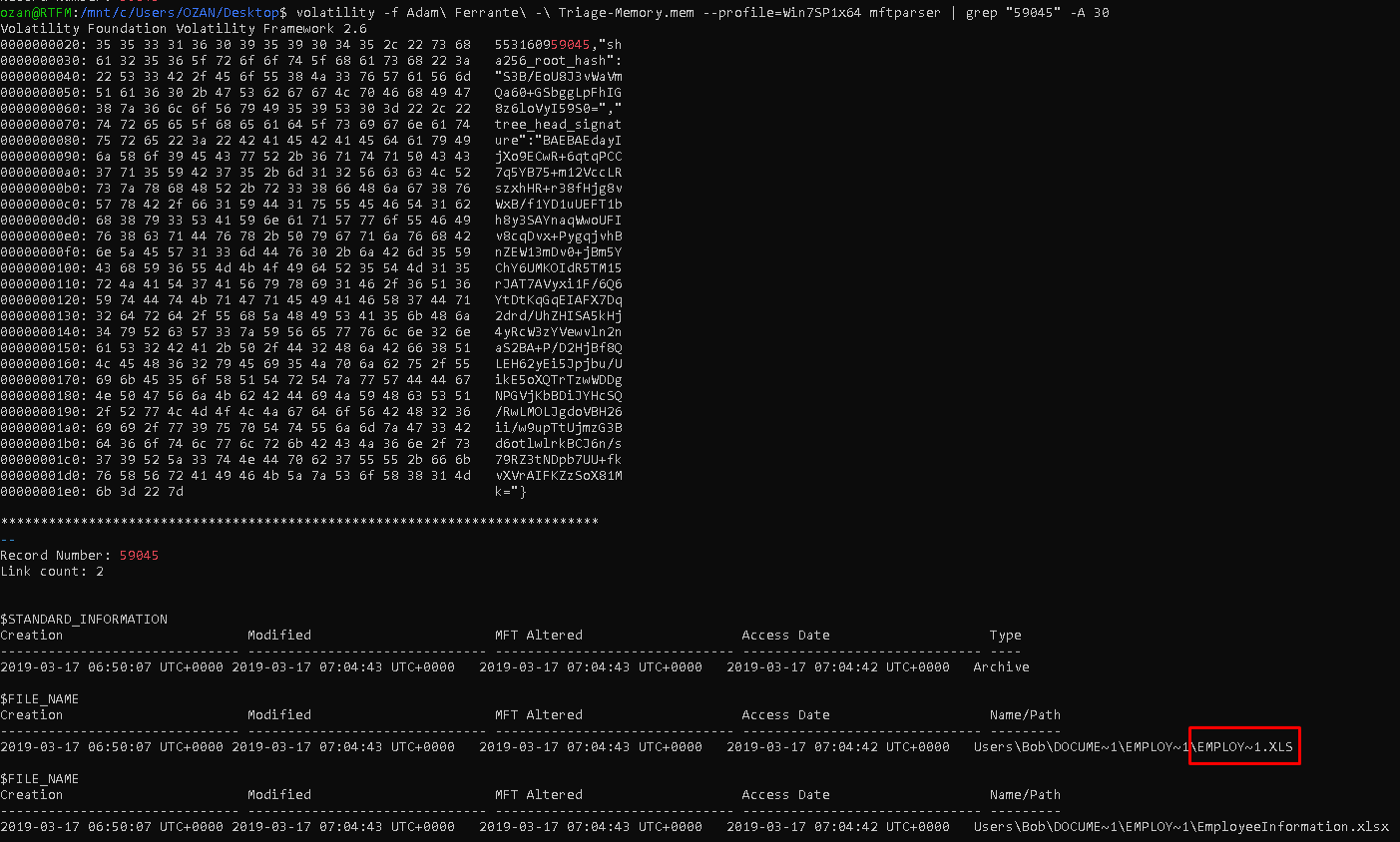
Flag<EMPLOY~1.XLS>
This question seemed to me as if they couldn't find any other questions to ask, let's ask it and pass it on anyway.
In the first questions we were able to detect the malware again by looking at pslist by looking at the pid, but to verify that we have taken a dump on the virustotal can also verify the accuracy.
Flag<‘3496>
Linux Forensics#
1.red star (10 Point)#
When we open the image file with Autopsy, it is seen that part 9 is a Linux system. While browsing the system, we can see which distribution is under boot.
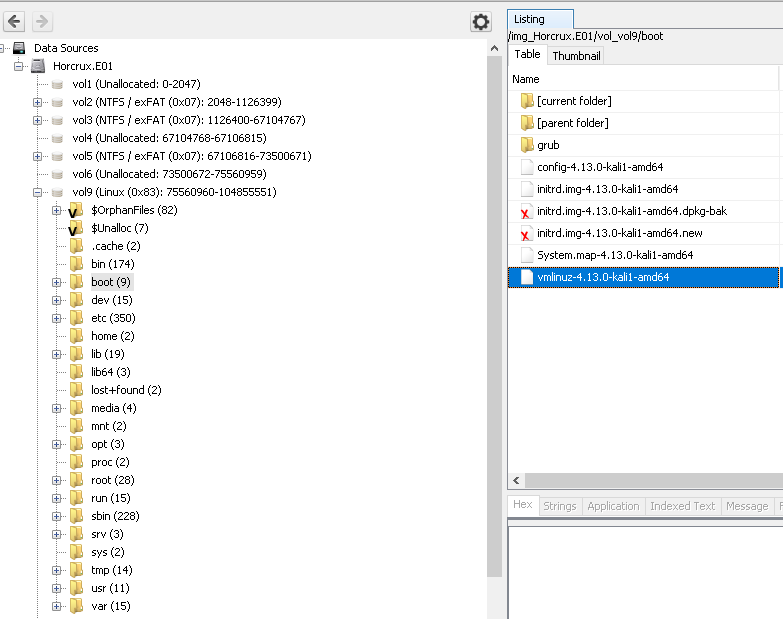
Flag<‘kali’>
2.abc123 (10 Point)#
In Autopsy just look at the log files.The log file can be accessed via
"/var/log/apache2/access.log".
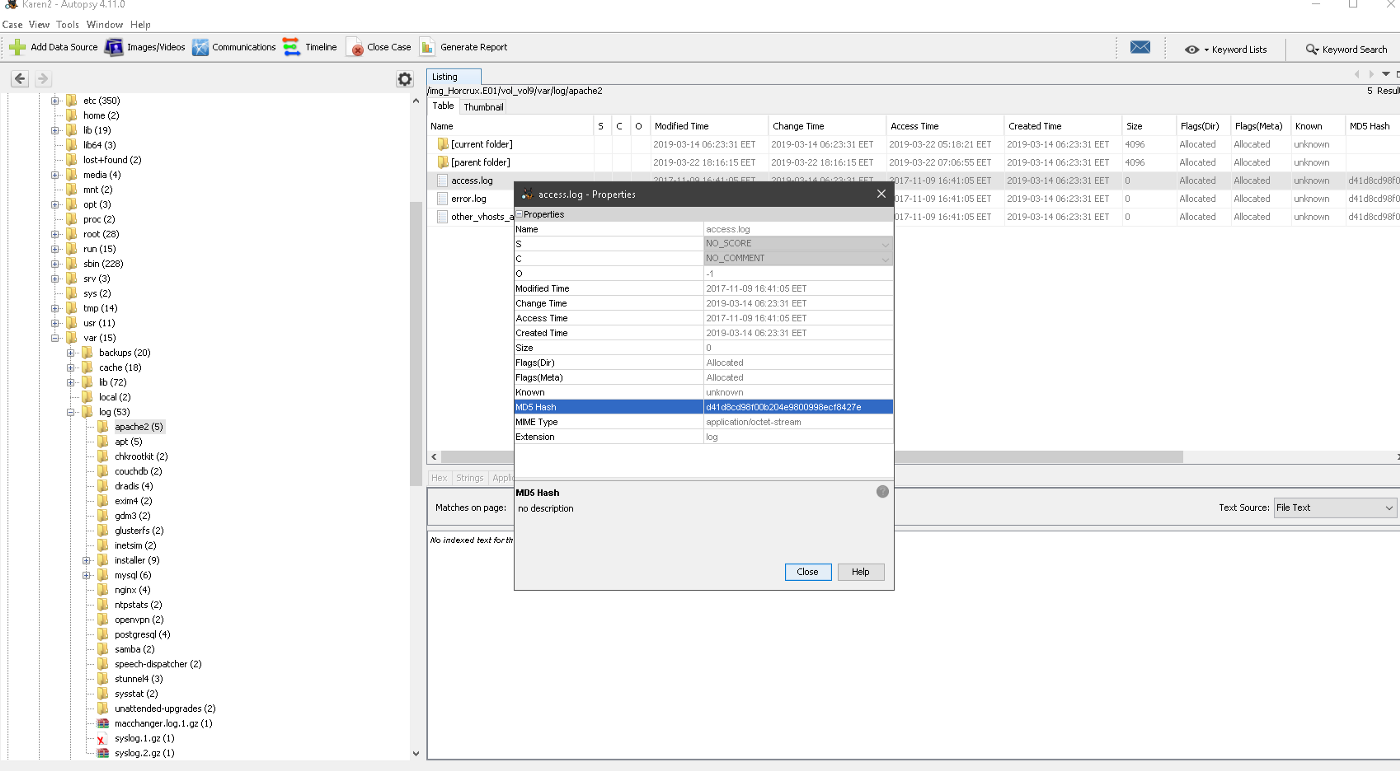
Flag d41d8cd98f00b204e9800998ecf8427e
3.Radiohead - No Surprises (10 Point)#
You’ve guessed more or less what we’re looking for. One of the most used tools for dumping password hashes. The first place to look for this will be the download folder, "/root/Download/” under the answer we’ll be looking for.
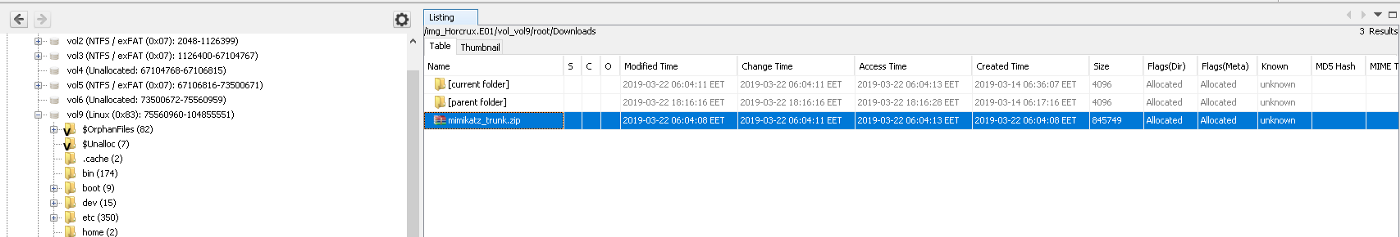
Flag<mimikatz_trunk.zip>
4.super duper secret (15 Point)#
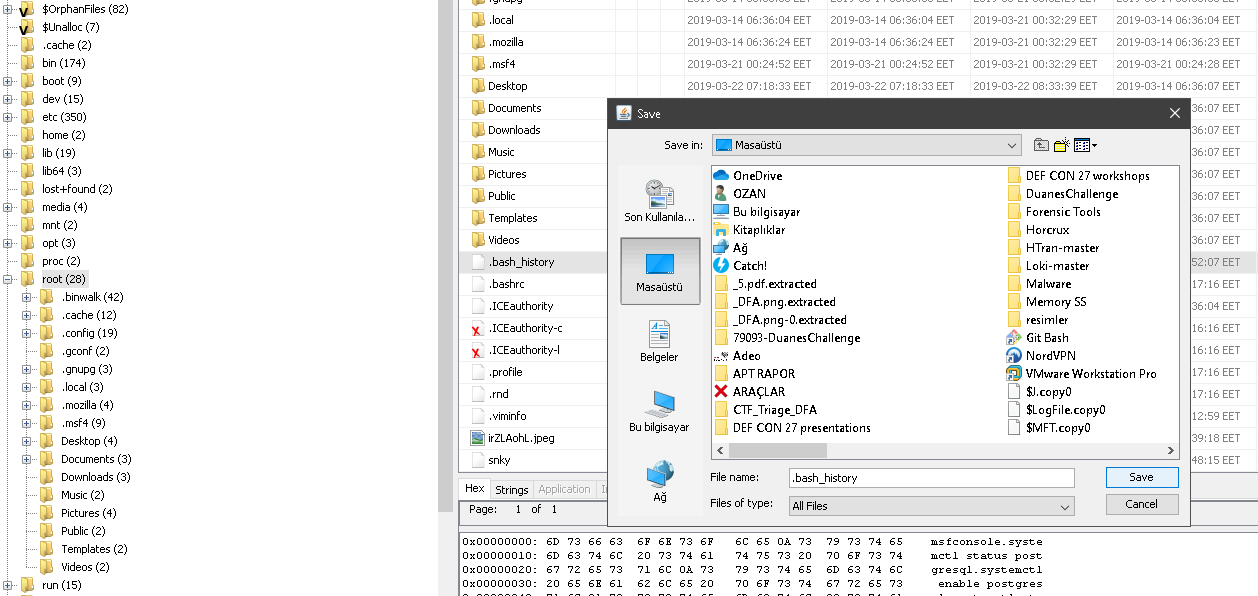
We had to learn the files created for this question, so I would find the bash_history file and take it out.
Later, when I opened it with the help of a text editor, I saw that a file named SuperSecretFile.txt was created in Desktop.
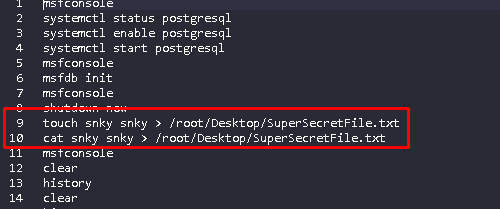
Flag<SuperSecretFile.txt>
5.this is a hard one (15 Point)#
Again, when looking inside bash_history it was seen that the vehicle used was binwalk.
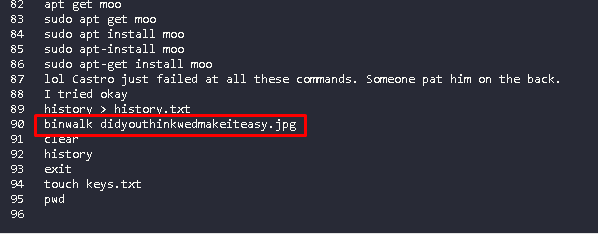
Flag Binwalk
overachiever (15 Point)#
I went through this question a bit and found the checklist under Desktop. I reached the flag when I opened it with the text editor by pulling it out.
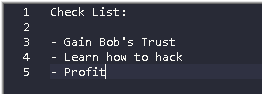
Flag Profit
In the first questions we found the hash value of apache2's log file. Again, the size of the file "/var/log/apache2/Access.log" sıfır is zero (0). in this case, we can understand that it was never run.
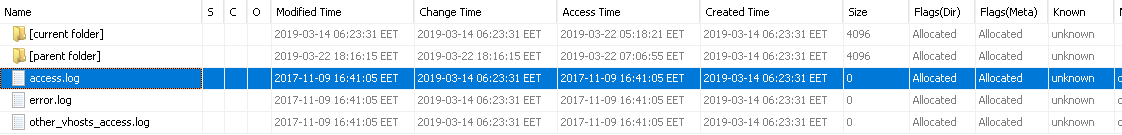
Flag<0>
8.oh no some1 call ic3 (25 Point)#
When I tried to go through the history file for this question, I realized that I was on the wrong track and started looking elsewhere.
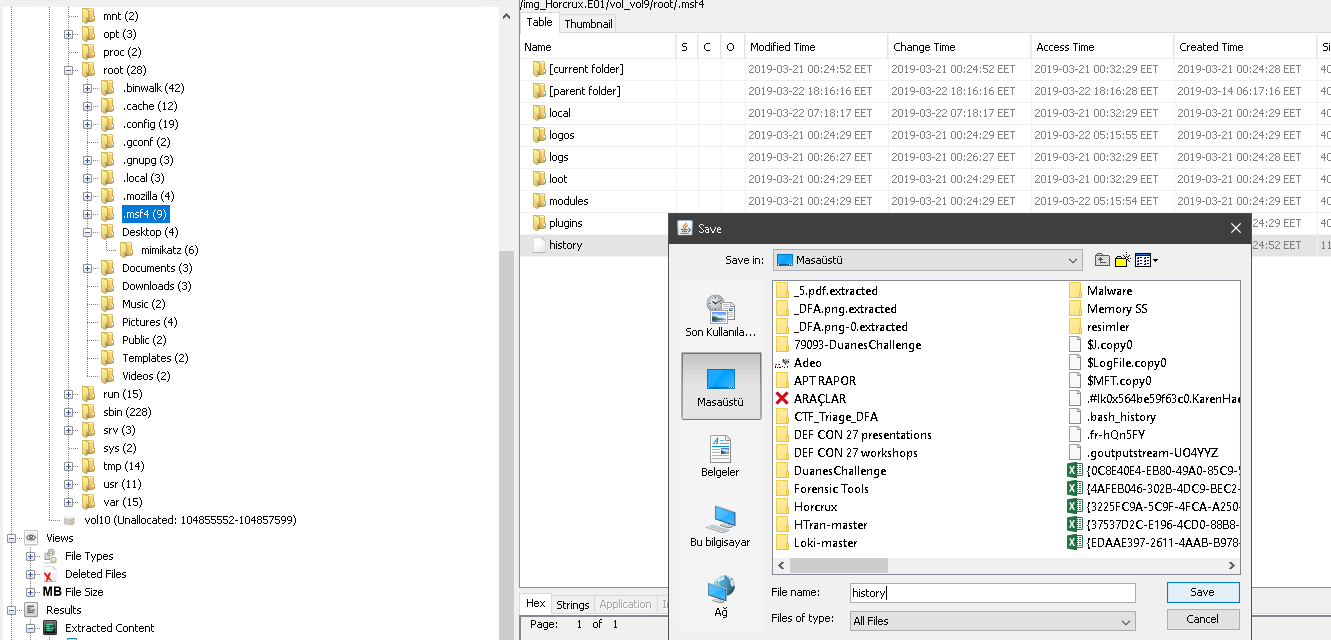
Later I realized that the answer I was looking for was a screenshot under root.
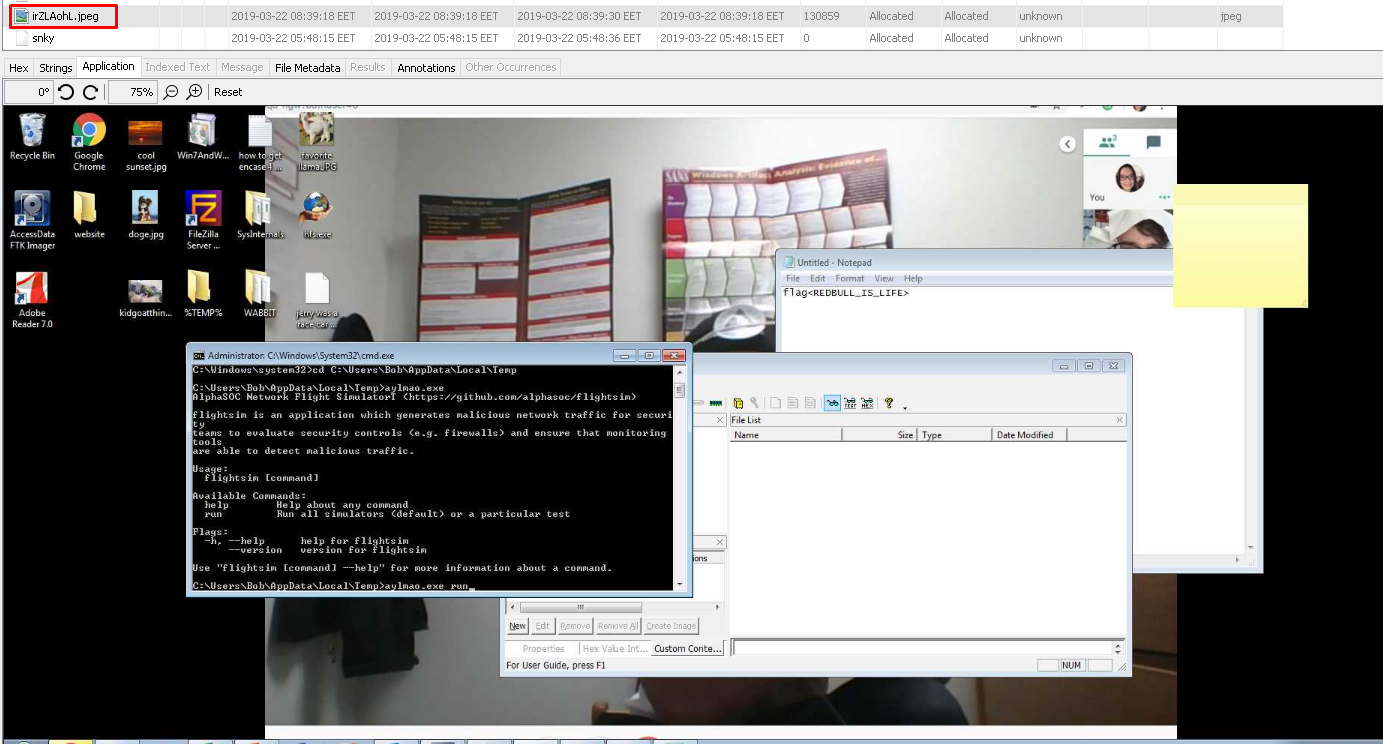
Flag<irZLAohL.jpeg>
9.scripters prevail (25 Point)#
While browsing the directories I came across a folder with the name myfirsthack under Documents.
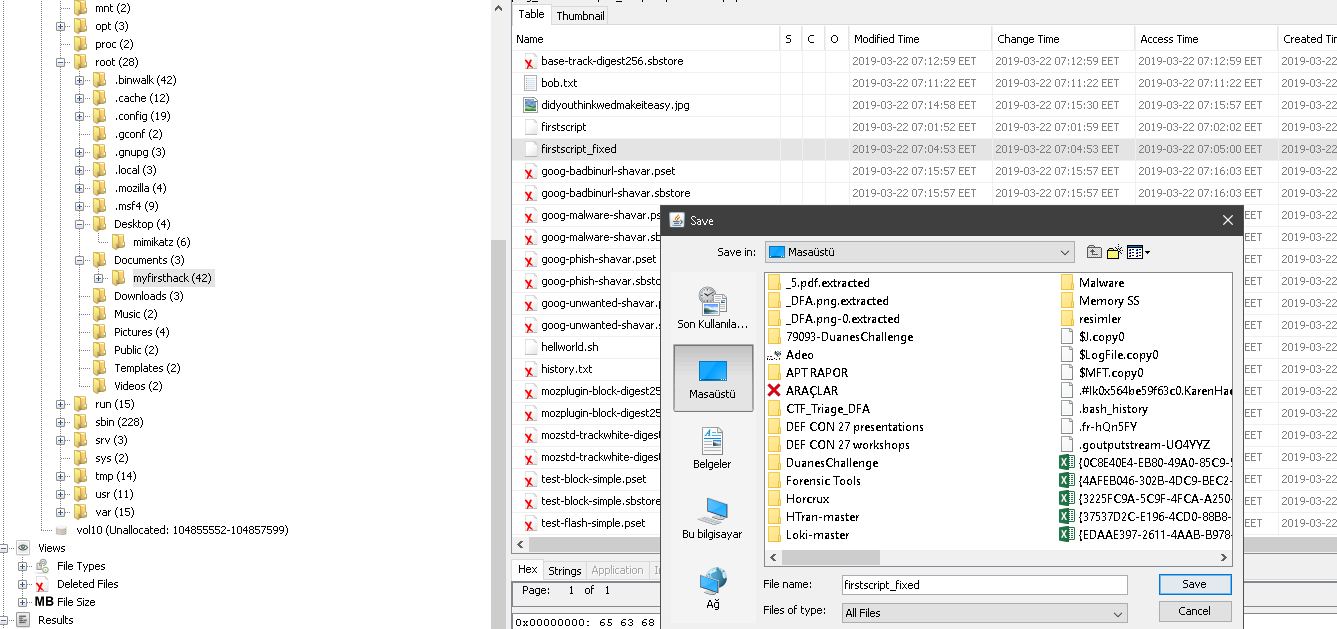
Here is the file "firstscript_fixed" caught in my eye and after opening it out,
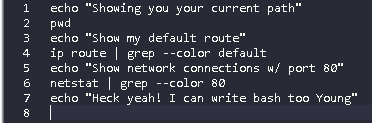
Flag Young
10.the who (30 Point)#
The only place we need to look here is auth logs. To do so, you need to export the file "/var/log/auth.log" and examine it with a text editor.
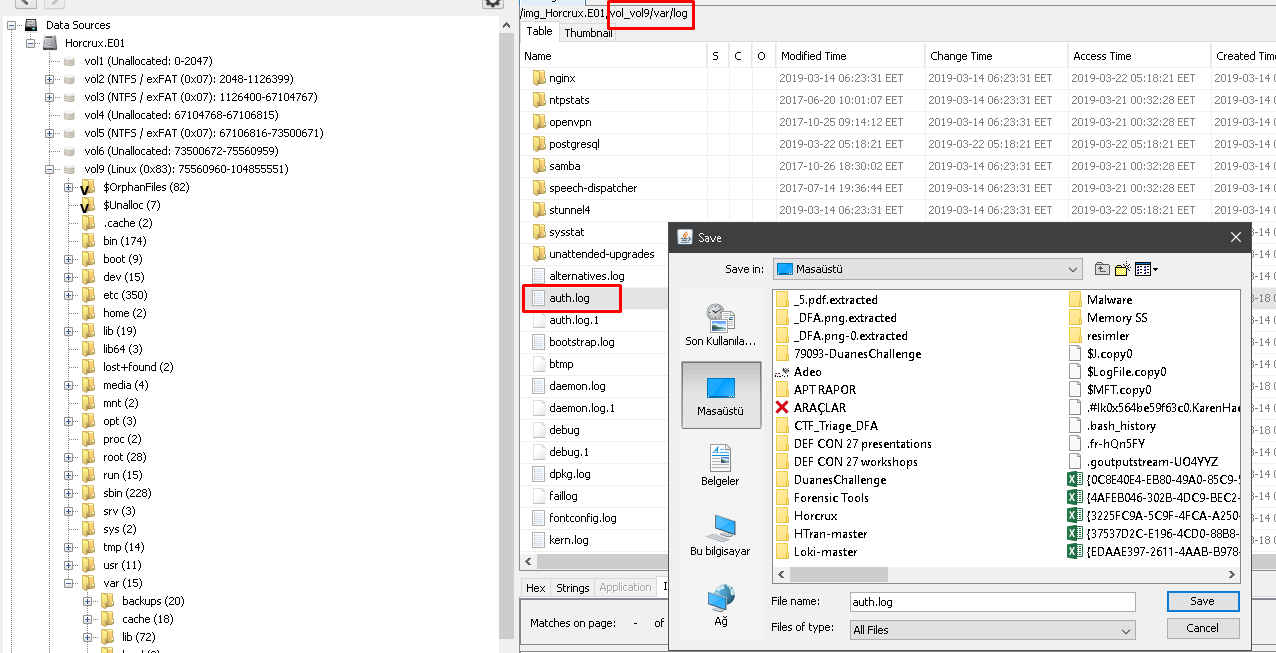
When we examine the times given to us, we identify the root user many times.
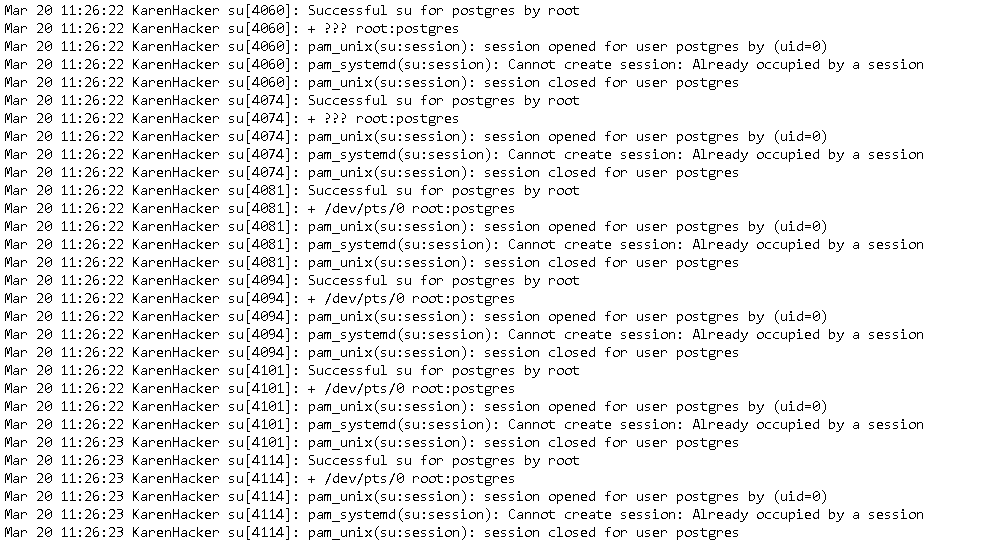
Flag postgres
11./ (30 Point)#
All we have to do is look at the bash_history site and find the last modified directory.
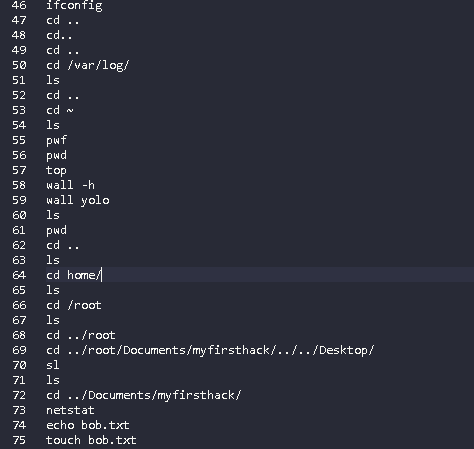
Flag< /root/Documents/myfirsthack>
Triage VM Questions#
1.Who’s That User?(1 Point)#
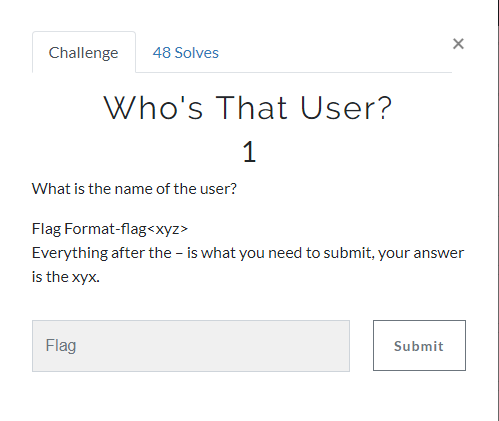
When we go to the "C: \ Users \" directory, we see that the user name is Bob.
flag bob
2. Thee who logged in last(5 Point)#
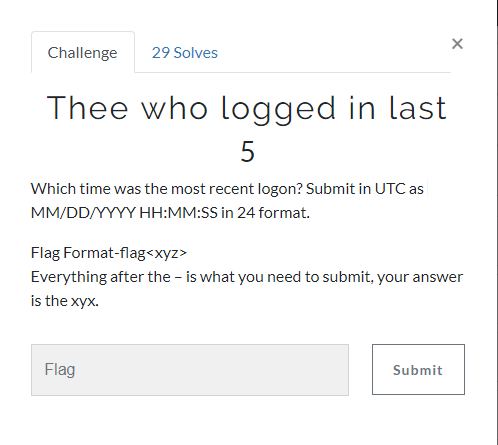
The last logon time on the computer is asked for this, we need to export the file "C:\windows\system32\ config\SAM" with FTK imager and parse it in RegRipper.
rip.exe -r ".\SAM" -f sam
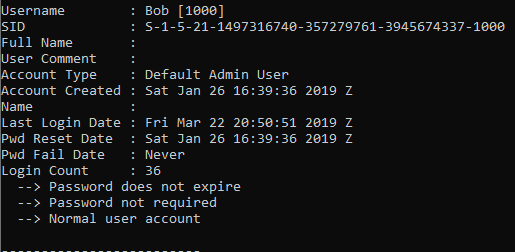
Flag<03/22/2019 20:50:21>
3. Down Time? More like Frown Time(5 Point)#
The last shutdown date of the computer can be accessed by exporting the file edip "C:\Windows\System32\ config\SYSTEM" with FTK Imager and using the -shotdown module in the Regripper.
1
| "rip.exe -r ".\SYSTEM" -p shutdown"
|
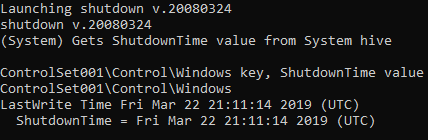
Flag<03/22/2019 21:11:14>
4. No one’s ever really gone… Palpatine Laugh(5 Point)#
He says it's a deleted 7z file. When we go to the $Recycle.Bin folder from FTK Imager or Autopsy, we see 2 deleted 7z files. When we export the files and open them with WinRAR, we see the CRC32 hash of the file directly.
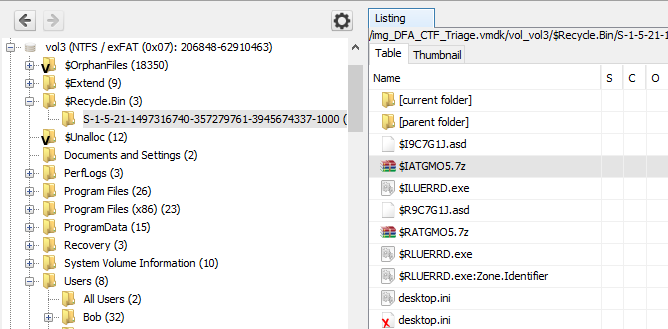
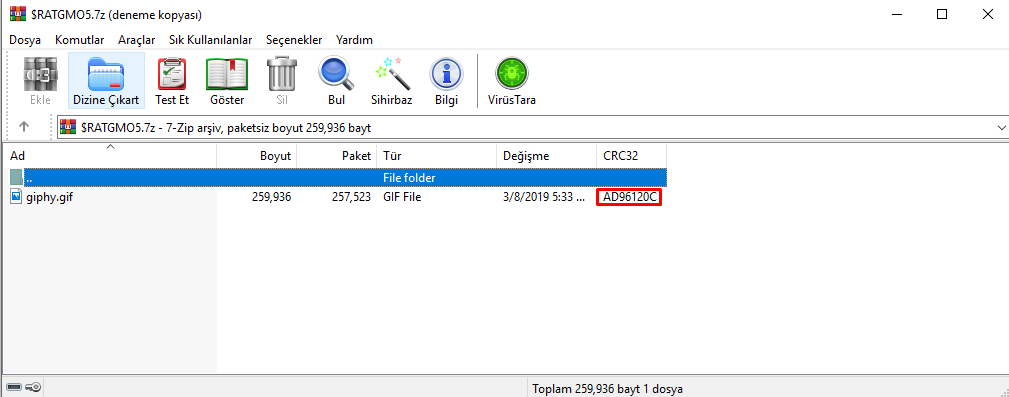
Flag AD9612C
5. Now, is no time at all(7 Point)#
We will also use RegRipper and SYSTEM hive for the computer's time zone.
1
| "rip.exe -r ".\SYSTEM" -p timezone"
|
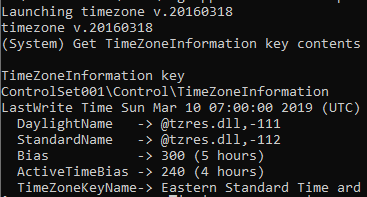
Eastern Standart Time UTC-5
Flag UTC-5
6. IT’S OVER 1000(7 Point)#
The user asks the user RID 1000 and how many users are greater than 1000. The command we used in question 2 actually gives the answer to this. Our answer is 1.
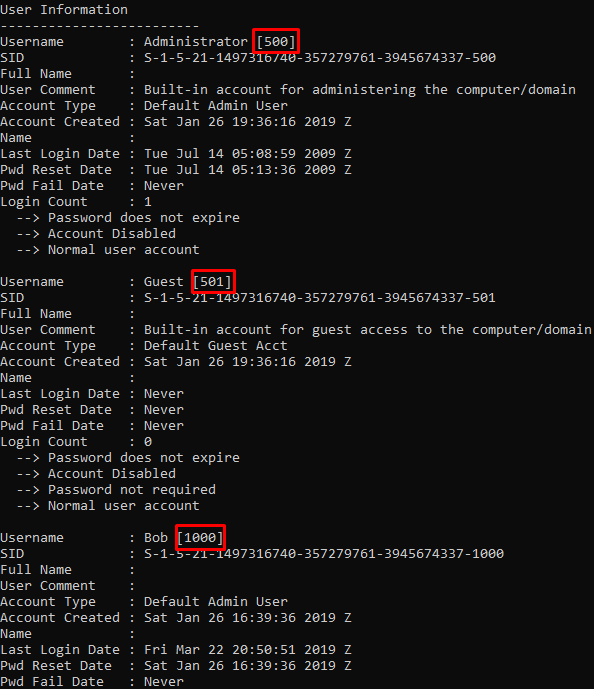
flag<1>
7.Go Go Gadget Google Extension(7 Point)#
To find extensions installed in Chrome, go to the directory "C: \ Users \ Bob \ AppData \ Local \ Google \ Chrome \ User Data \ Default \ Extensions". The folder names here are the extension ids. When we examine these folders, we see that one extension is different from the others.
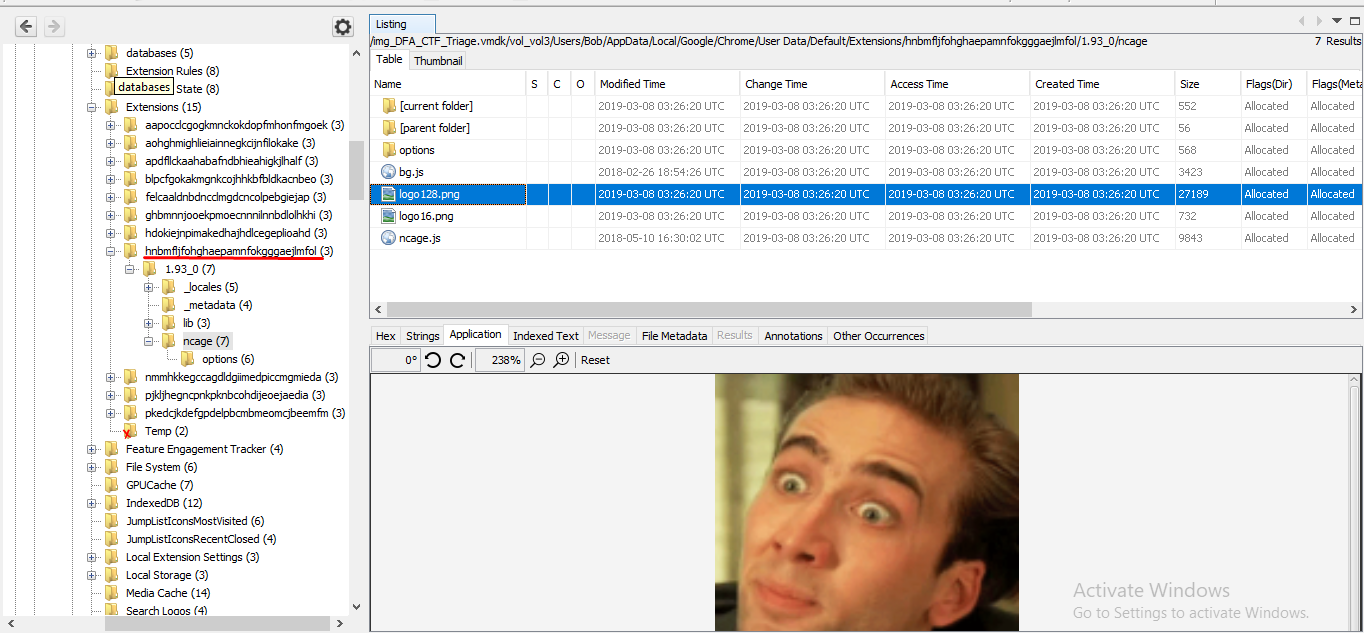
flag hnbmfljfohghaepamnfokgggaejlmfol
8. Run, Adobe, Run!(7 Point)#
There are many places we can look for this question. If we parse the NTUSER.DAT hive with RegRipper userassist module, we can see it run. "C:\Users\Bob\NTUSER.DAT"
1
| "rip.exe -r ". \NTUSER.DAT" -p userassist | findstr Adobe"
|
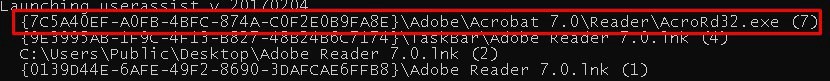
Flag<7>
9. Should I use my invisibility to fight crime or for evil?(10 Point)#
When we go to the desktop there are two .exe wants us to be hidden. From FTK we can find out which file is hidden by looking at the file details.
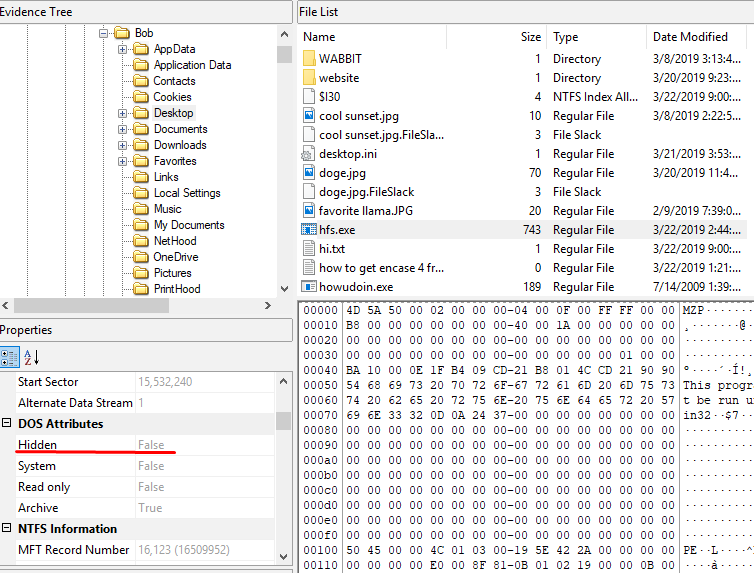
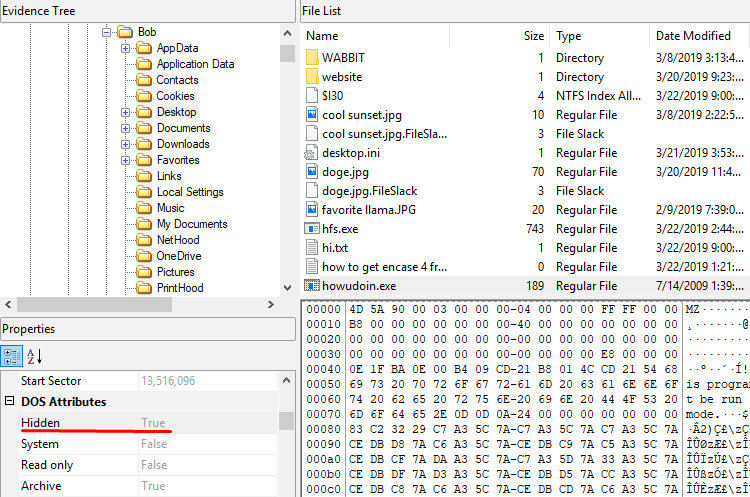
flag<howudoin.exe>
10. It’s all in the timing(10 Point)#
Export the history file of Google Chrome and open with the "ChromeHistoryViewer" and searching "placeholder.com" will give the answer.
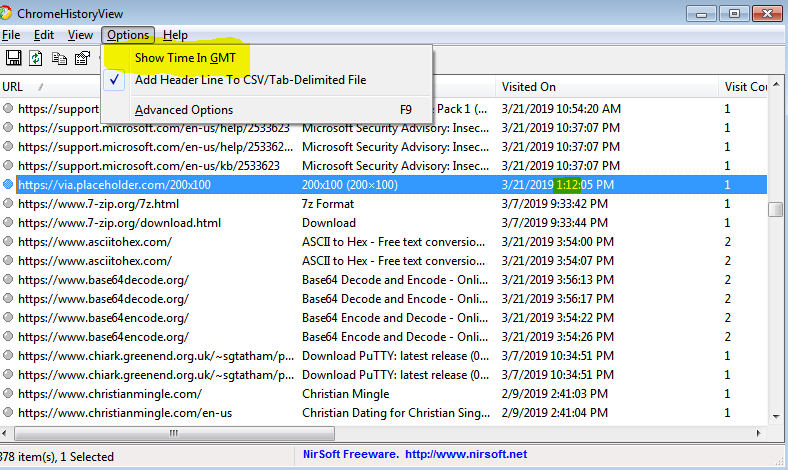
Flag<01:12>
11.The Hostess with the Mostest(10 Point)#
We can find the name of the computer from the SYSTEM hive again using RegRipper's compname module.
1
| rip.exe -r ".\SYSTEM" -p compname
|
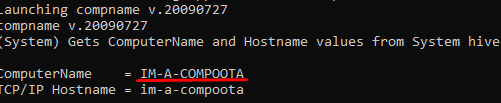
Flag IM-A-COMPOOTA
12. These messages aren’t gonna message themselves!(10 Point)
#
Looking at the files downloaded from the “C:\ UserS\ Bob\ Downloads” directory;
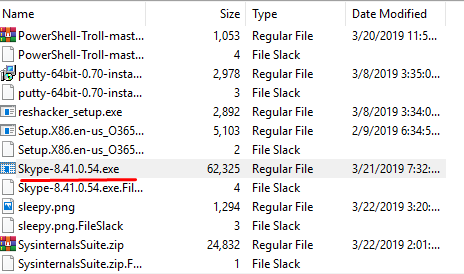
Flag skype
13. Dang it Bobby - (15 Point)#
We'll use ChromeHistoryView again

Flag<‘3>
14. Damnit Bobby!(15 Point)#
When we enter Bob's Documents Folder, we see a folder named "EmployeeDocument". If we export the "EmployeeInformation.xlsx daki file here.
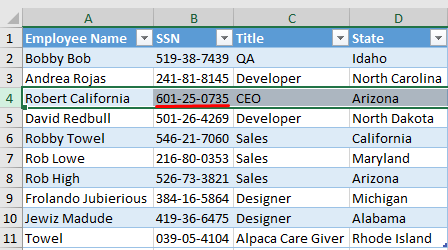
Flag<601–25–0735>
15. Get back to work Sponge Bob me boy(18 Point)#
The network capture showed the video ID to be N9NCyGaxoDY. What is the title of the video?
1
| This seems to be the Youtube id. "https://www.youtube.com/watch?v=N9NCyGaxoDY"
|
If we go to, we’ll get Bob’s video.
Flag<Rowan Atkinson Toby the Devil - Welcome to Hell>
16. Laughs in Hidden(25 Point)#
The extension of one of the files on the desktop has been changed. If we look at the indexed Text section of this file from Autopsy, we see that this file is actually a powerpoint presentation with a .pptx extension. We can export this file and calculate the CRC32 hash.
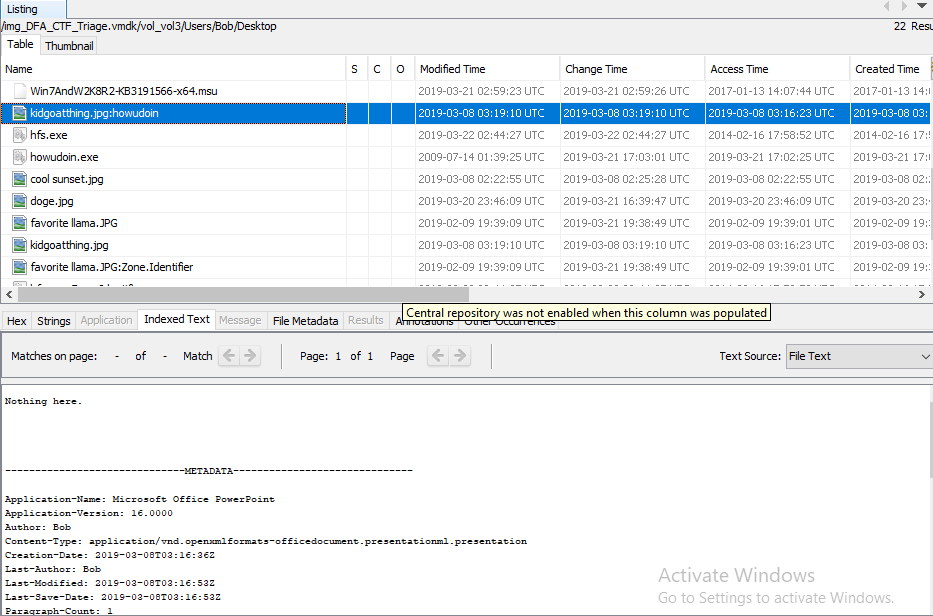
Flag<076A3AF5>
17. Desktop Flag 1: Just the start of the fun(25 Point)#
Viewing this file in Autopsy or FTK is enough to find a flag.
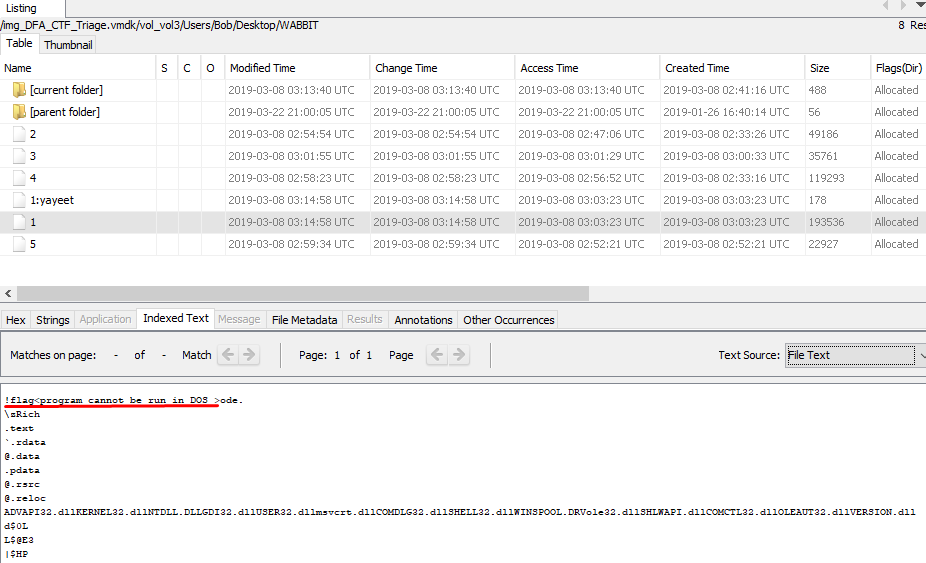
Flag: program cannot be run DOS
18. Desktop Flag 2: Electric Boogaloo(25 Point)#
If we open the file with HexEditor, we see that it says NETSCAPE2.0, and that the Header part of the file consists of 00s. When we search for NETSCAPE2.0 on google, we understand that this file is a .gif file. However, the header information has been changed. We need to change the header information as the header of the .gif file should be.
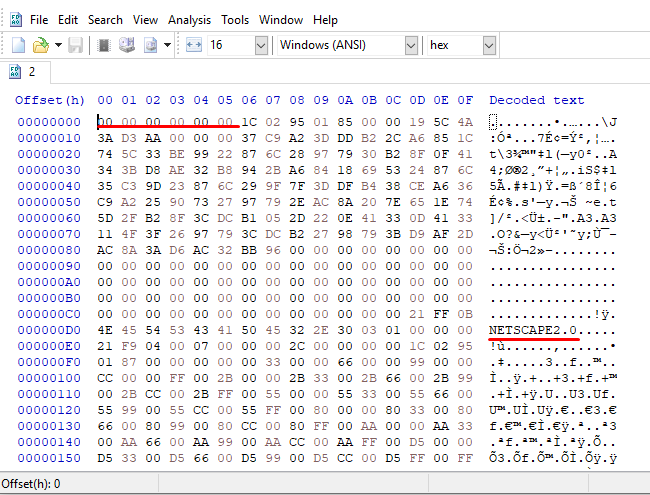
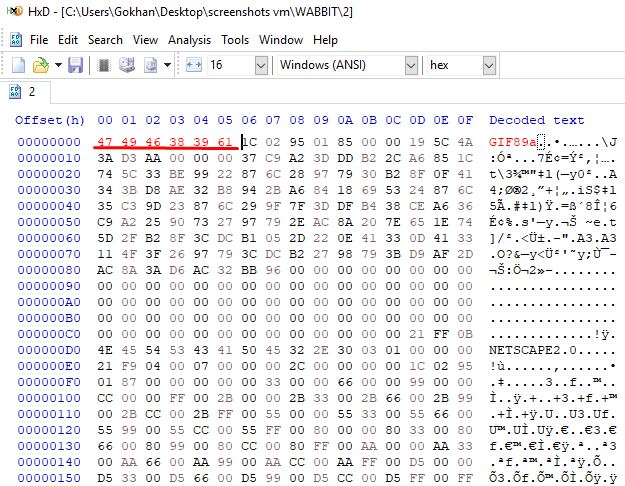

Flag<taco_bout>
19. Desktop Flag 3: Need for Speed(25 Point)#
When we open the file in Hex Editor, we see a link. When we go to this link, a picture comes from a concert called Dragonforce .
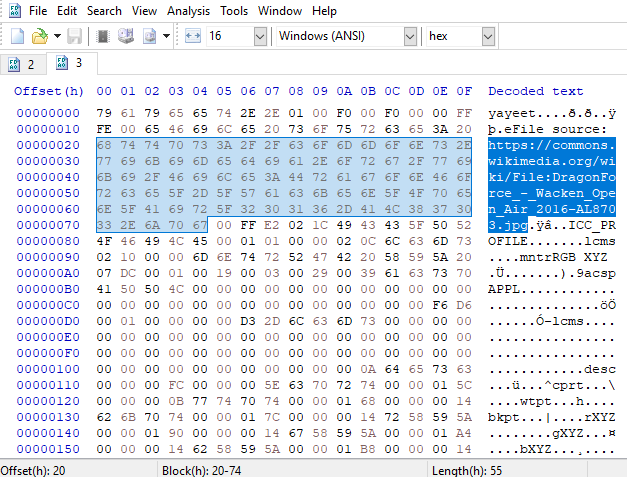
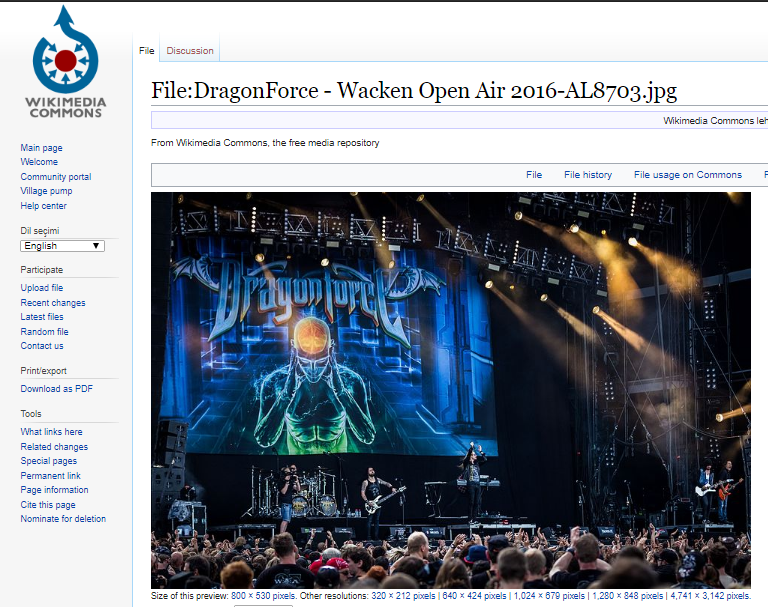
Flag: Dragonforce
20. Desktop Flag 4: Want some more?(25 Point)#
When we open the file with Hex Editor, the file looks like a ".jpeg"file, but it looks like it has been tampered with.
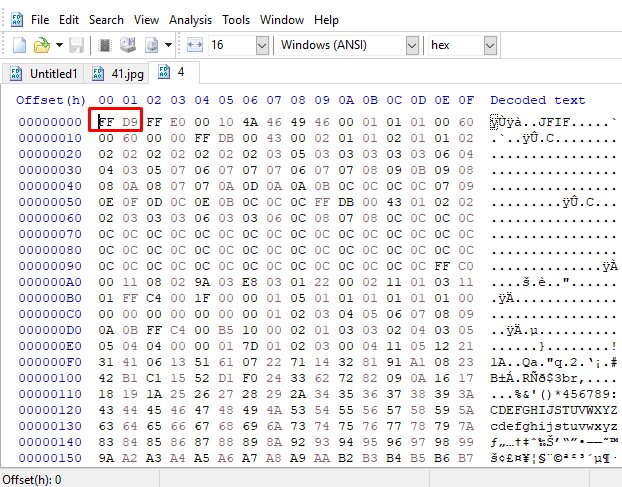
When we check the footer value of the file, we see that it has also been changed
When we correct these values
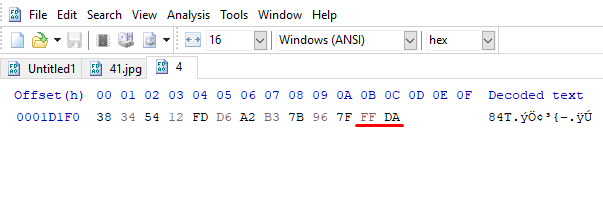

Flag<wof_on_champ>
21. Now watch me youuuuuuuu(25 Point)#
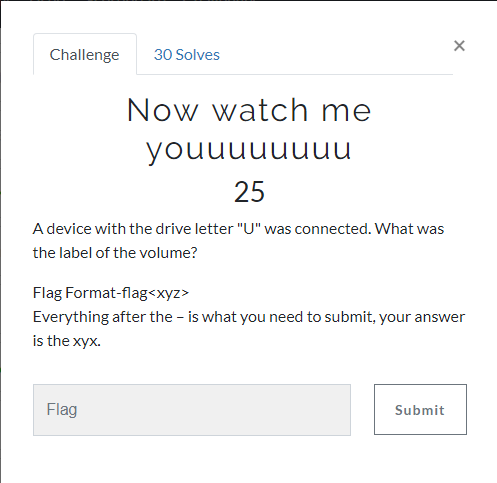
It asks for the name of a connected device. We can also find this in the registry. But there's an easier way;
1
| "C:\Users\Bob\AppData\Roaming\Microsoft\Windows\Recent"
|
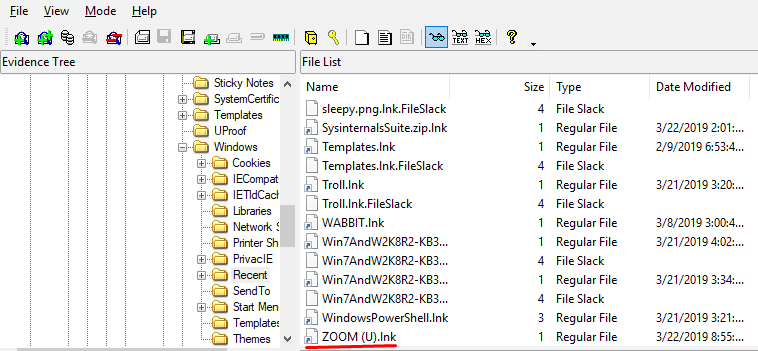
Flag: ZOOM
22. Desktop Flag 5: No, you can’t have more time(30 Point)#
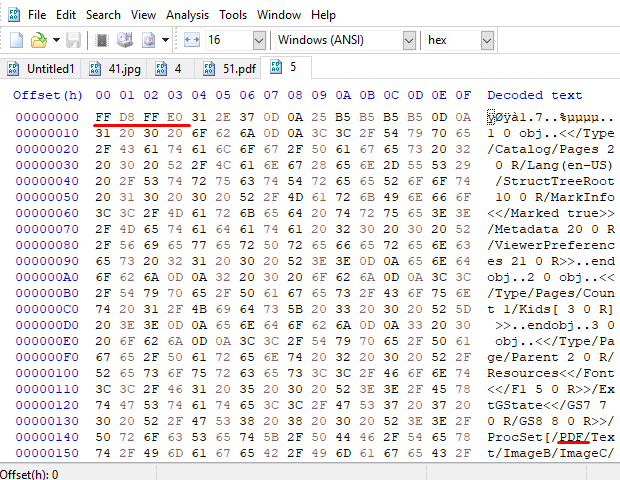
File Signature has also been changed in this file. When we open the file with HexEditör, we see that the file is a PDF file.
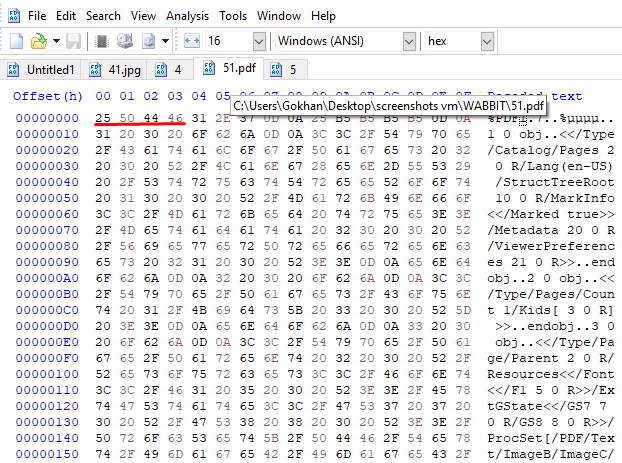
If we edit and open the file signature value as PDF, we see a white text inside the PDF.
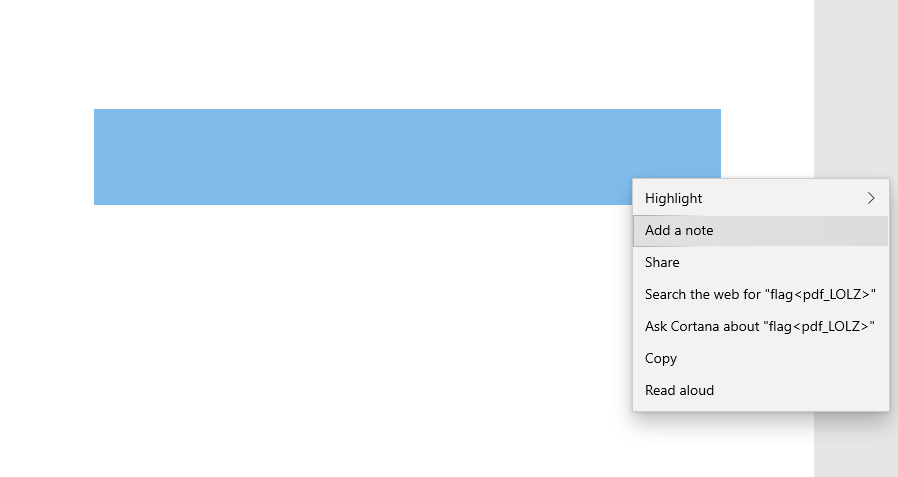
Flag<pdf_LOLZ>
23. I will look for you, I will find you… and I will hash you(30 Point)#
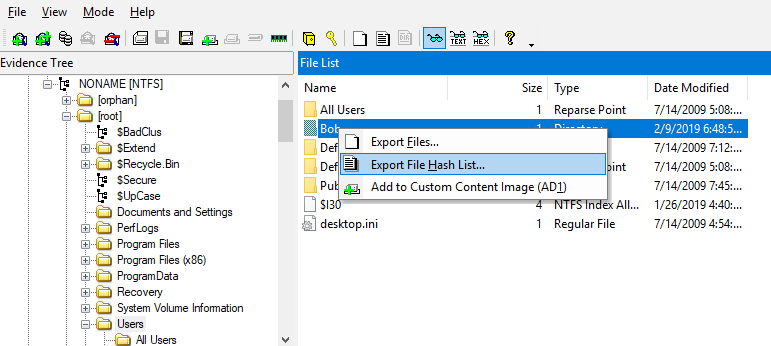
MD5 Hash value given the name of a file is requested. We will use the Export File Hash List feature of FTK Imager. Since it takes a long time to retrieve all the files on the disk, it can be started from frequently used folders such as Desktop and Documents. I chose the "C:\ User \Bob" folder.
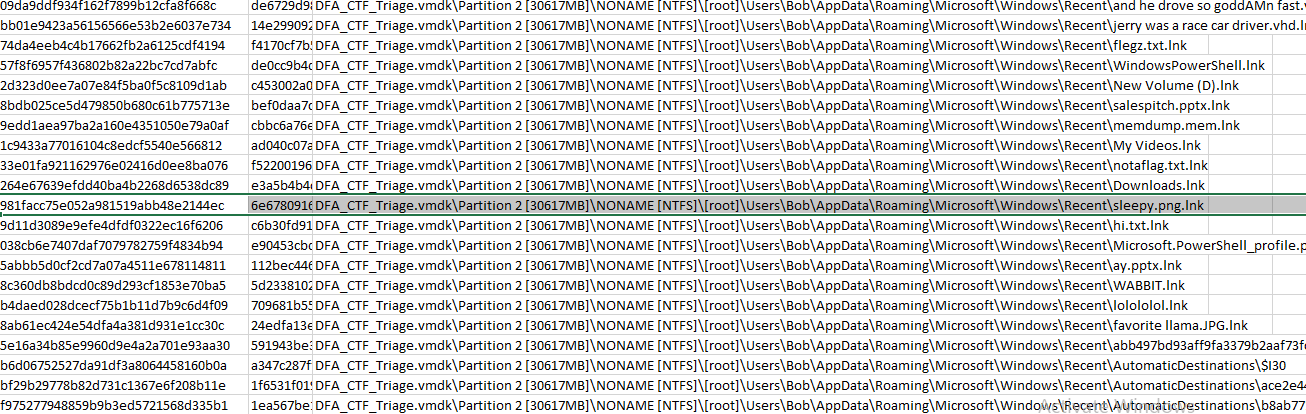
Flag<sleepy.png>
24. Easy Peasy Lemon Squeezy(40 Point)#
When we open this "sleepy.png" file, which we found in the previous question and have a desktop background, we see the flag on the sticky note.
Flag: holla
25. Can you like… not?(50 Point)#
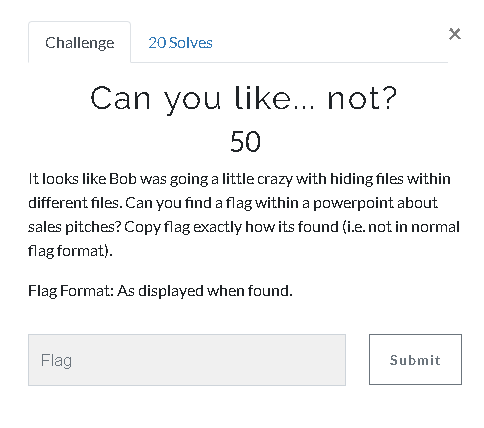
We saw such a file in the "Recents" folder, which we reviewed in the previous USB question. Looking at the "Documents" folder before searching the file extension saves us time. When we go to Documents folder, we see "salespitch.pptx" file.
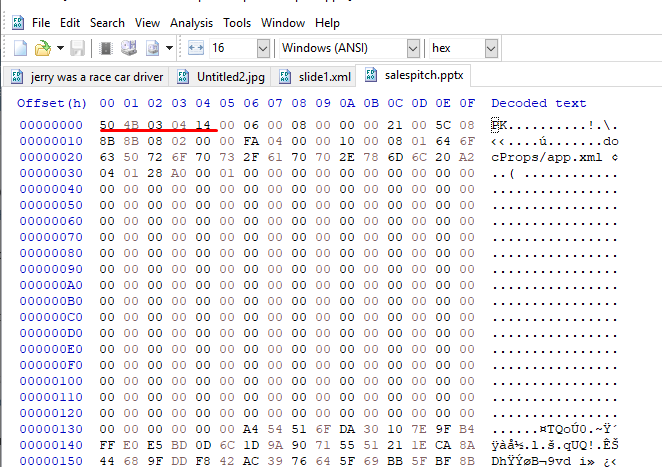
When we look at the File Signature value of the file, we see that the file is actually a ".zip" file. Extracting files and looking at strings we find the answer.
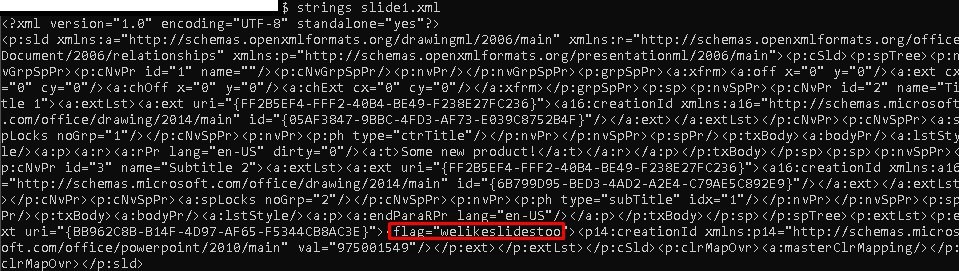
Flag: welikeslidestoo
26. KA-CHOW(100 Point)#
When we open this file with Hex Editor we see that it is very long. Scanning with Binwalk may make sense;
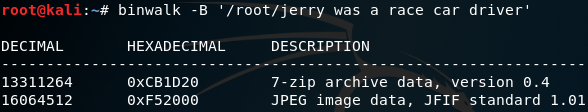
When we scan File Signature with Binwalk, we see that there are 2 different files in the file.
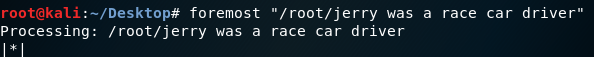
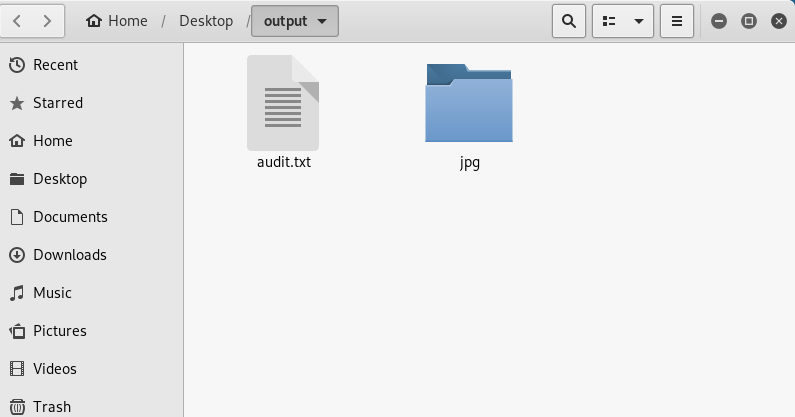

When we tried to extract these files, the .7z file could not be extracted while .jpg was exiting. This may be because the .7z file does not have a "Footer" value. When we look at the file "00031376.jpg" it says "he never win no checkered flag.. When we do a Google search, we come across a song called erry Jerry Was A Race Car Driver ve and we see that this text in the picture is quoted from the lyrics. Returning to the 7 .7z "file;
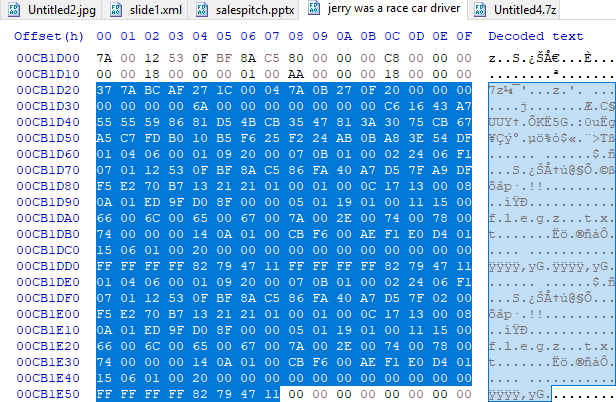
In HexEditor, we searched for a 7 .7z "file signature and found where the file started, but since there are no footer information in the .7z files, we will extract the file by guessing it. There is already a file named 'flegz.txt" in HexEditor.
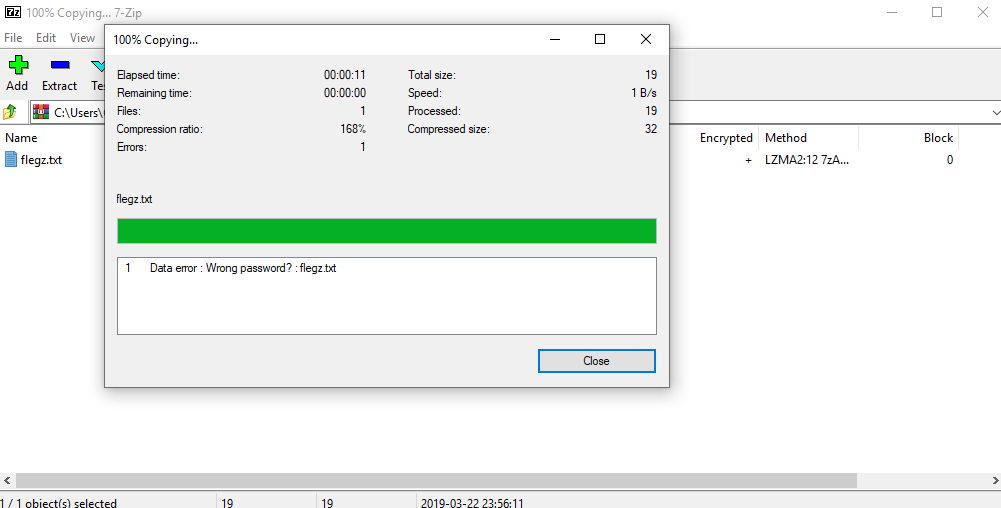
When we try to extract the file, we see that it is encrypted. When we try the song we see in the picture;
We get a wrong password error, the file opens when we try the song "But he never did come in last".
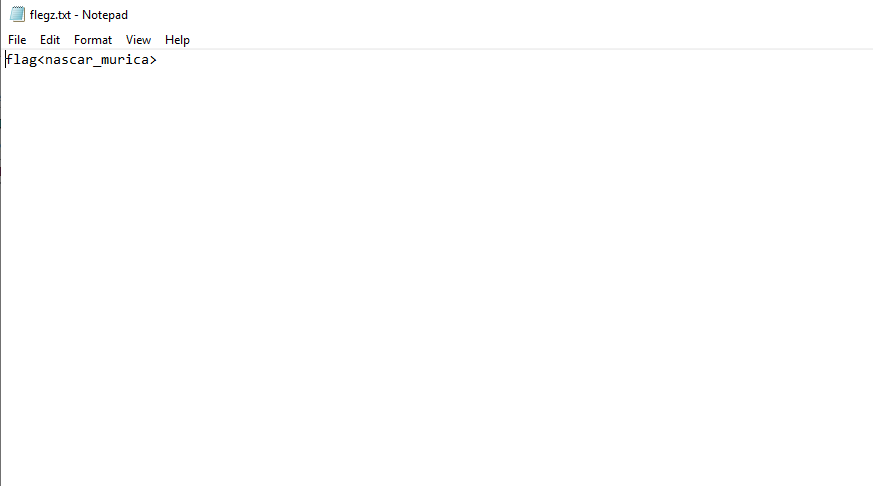
Flag<nascar_murica>
Deadbox Forensics#
1.Hello, my name is… (1 Point)#
When we open up the text that comes up with image file we can see the examiner.
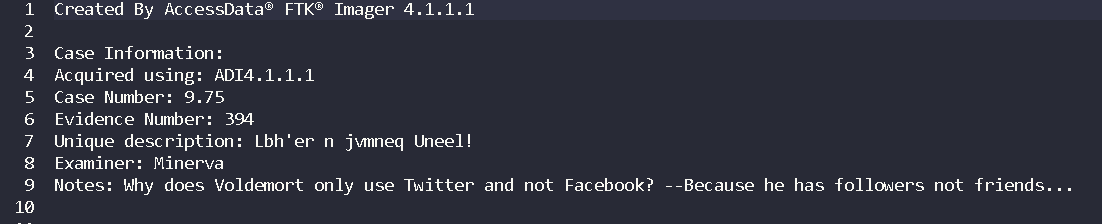
Flag< Minerva >
2.Who owns it? (1 Point)#
When we open up the image file "Autopsy" or "FTK imager" we need the analysis the "SAM" file and we can find what is the user name.
1
| "C:\Windows\System32\config\SAM\"
|
When we export the file we can parse with the “Regripper”
1
| "rip.exe -r .. \SAM -f sam"
|
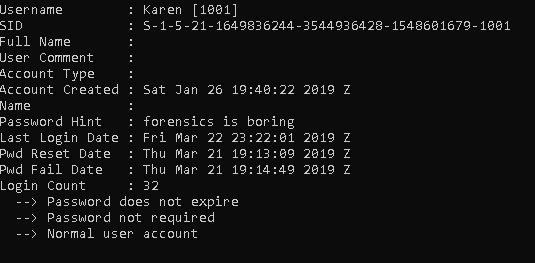
Flag< Karen>
3.Does it match? (1 Point)#
Same as first question we need the open the text file that comes up with image.
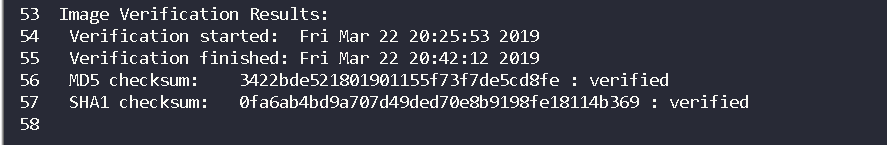
Flag<“0fa6ab4bd9a707d49ded70e8b9198fe18114b369”>
4.The Big Bang (1 Point)#
In this question we can use "ewfinfo" command on "Linux" and we can see file meta data.
Ewinfo Horcrux.E01
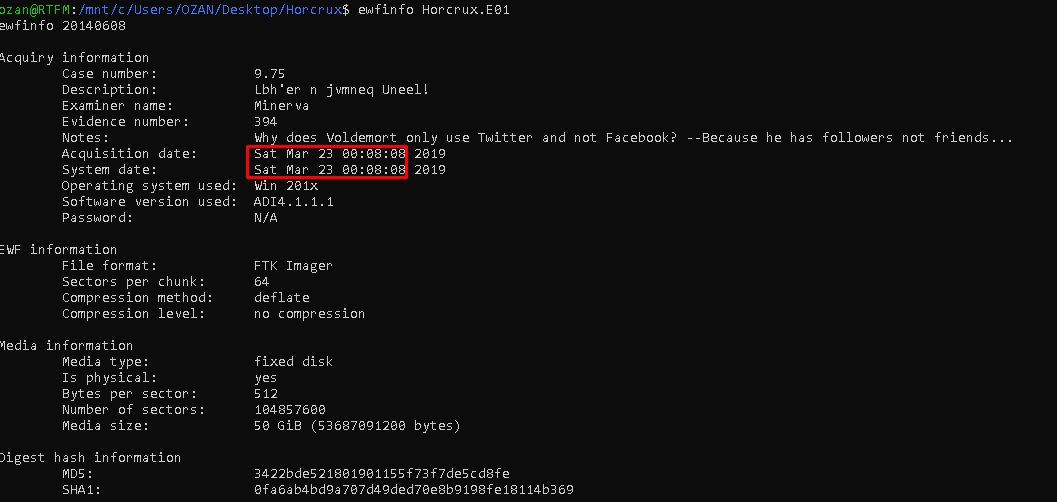
Flag<03/23/2019 00:08:08>
5.Which window is it? (5 Point)#
We need "SOFTWARE" registry hive to learn which Windows version. When we export the "C:\Windows\system32\config\SOFTWARE" we can parse with "Regripper"
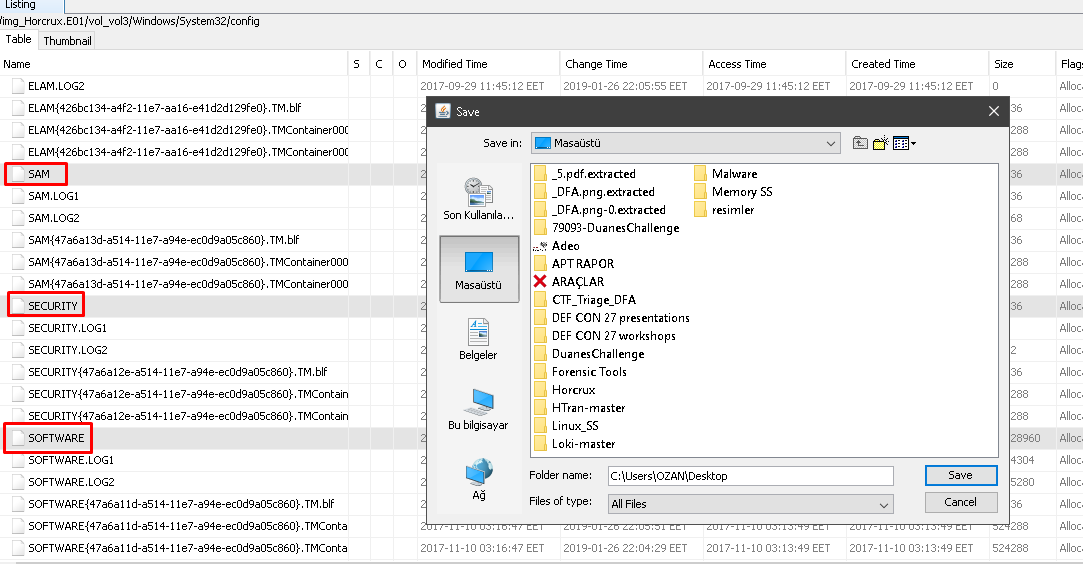
1
| rip.exe -r ..\SOFTWARE -p winver
|
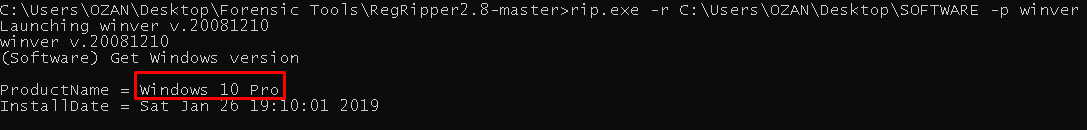
Flag<10>
6.The worst thing about prison were the dementors!(5 Point)#
I solved this question much later than others, because they had something they wanted to tell us from the beginning.
Minerva ->Minerva McGonagall
Horcrux ->An object with a part of a witch or witch spirit.
Dementors ->Dementors
Although I am a big Harry Potter fan, I was a little upset that I had worked so hard on this question :)
Flag< Harry Potter>
7.Brooms aren’t just for sweeping (5 Point)#
Again back to text file that comes up with the image.
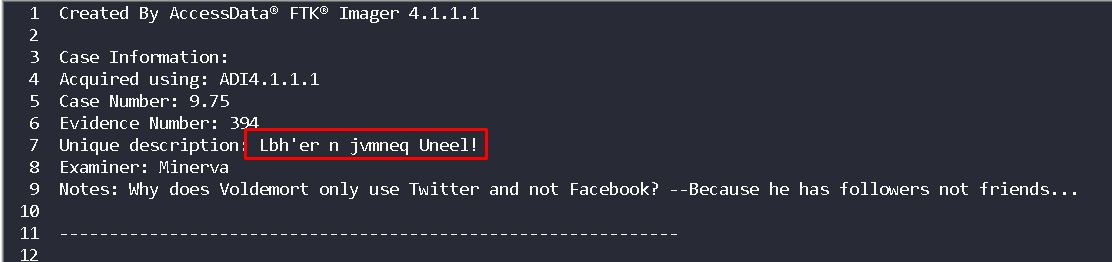
This looks like ROT13 encryption.
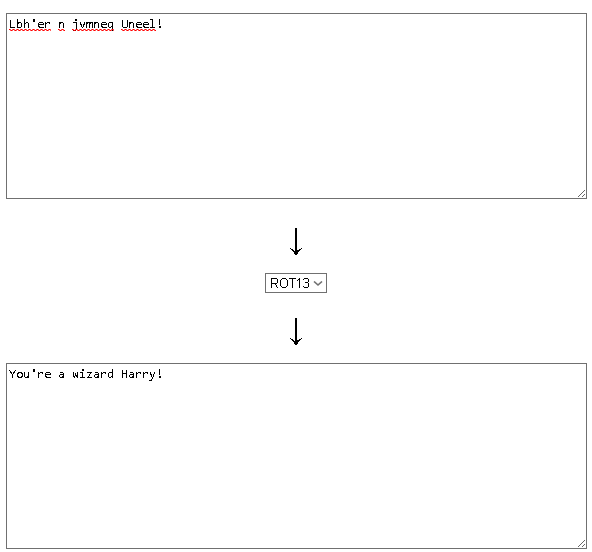
Flag< You’re a wizard Harry!>
8.Russia (10 Point)#
We can solve this question with Autopsy under the "OS Information"
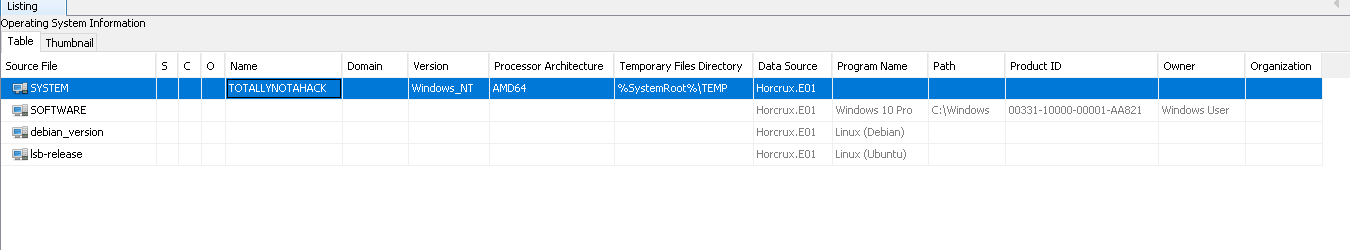
Another way is we can export "SYSTEM" hive and parse with the "regripper"
1
| "rip.exe -r ..\SYSTEM -p compname"
|
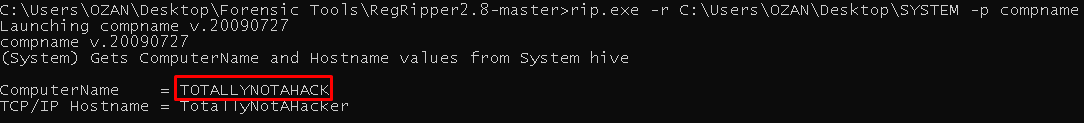
Flag< TOTALLYNOTAHACK>
9.Let’s chat (10 Point)#
We can see the web history or installed apps with the "Autopsy"
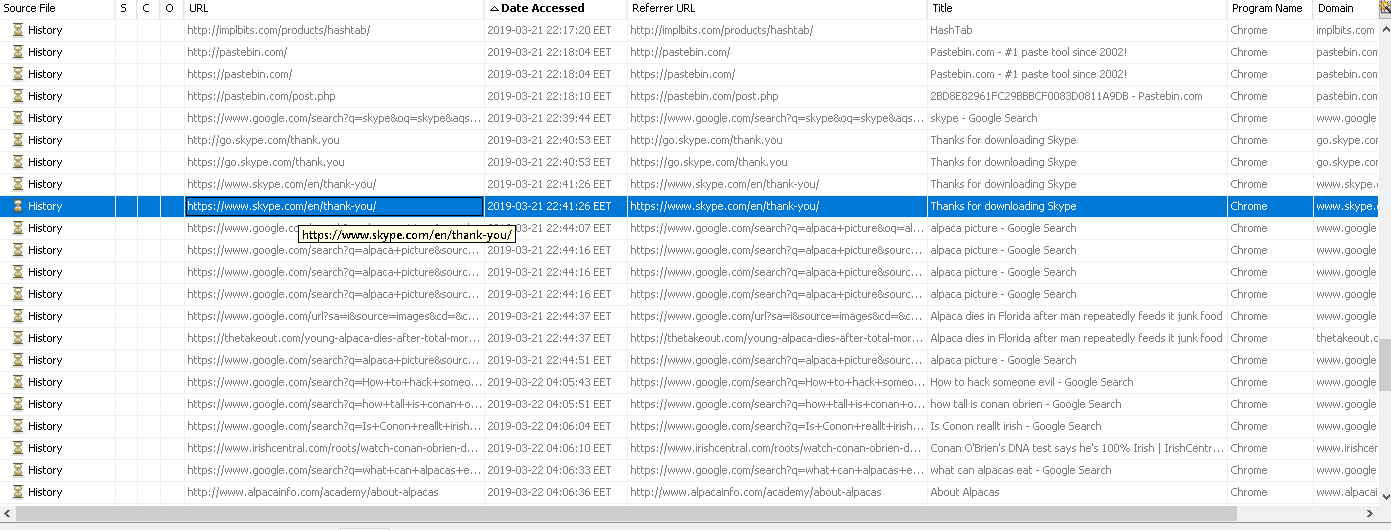
Flag< Skype>
10.Zippy Zip (15 Point)#
Again with the "Autopsy" we can see the zipcode on the "Web Form Autofill"
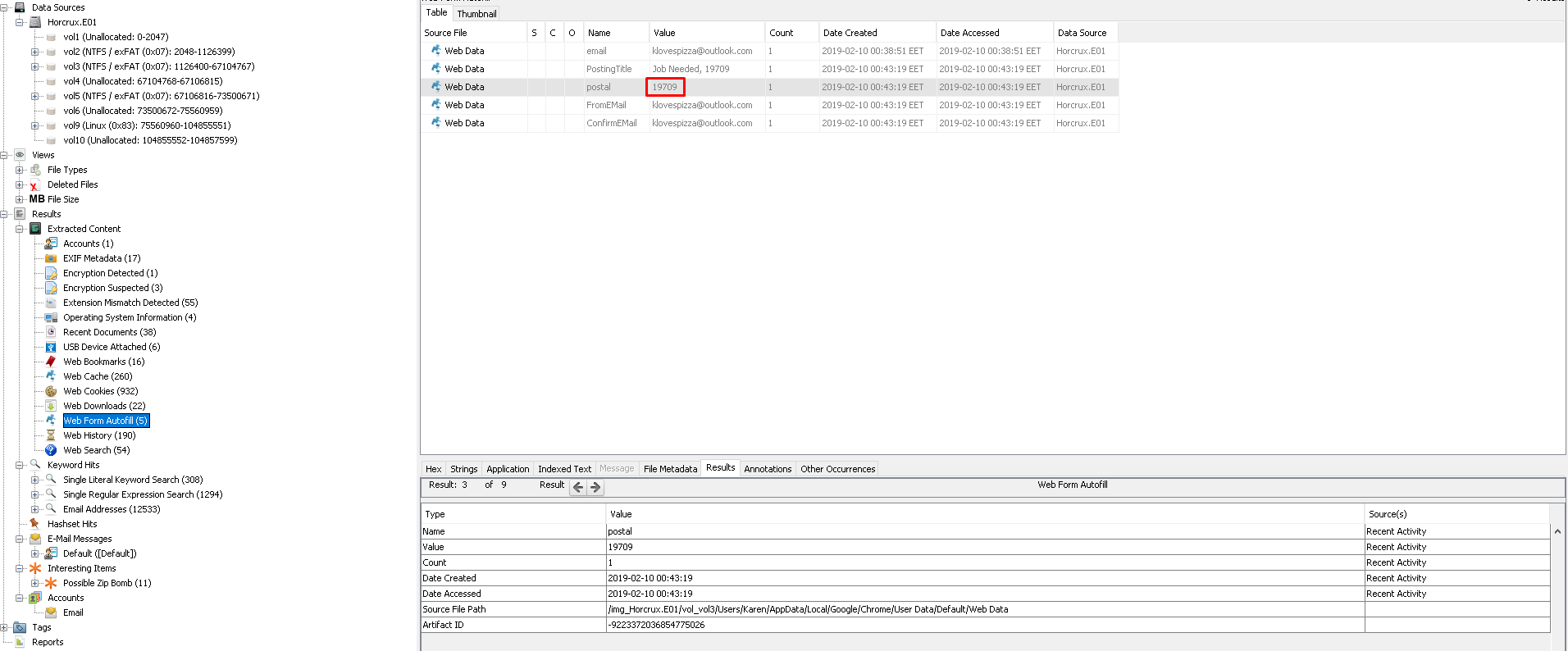
Flag< 19709>
12.New email, who dis? (15 Point)#
Previous question we got karen's e-mail adress with the "Web Form Autofill" when we search the e-mail adress on "Autopsy" we find a OST file.
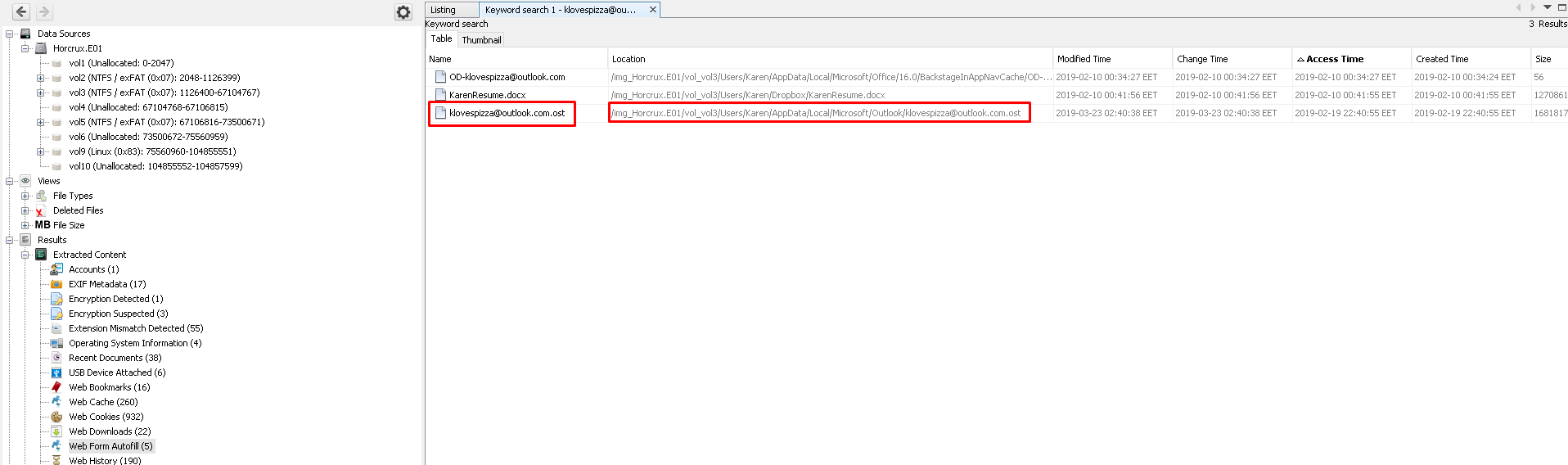
We need the extract this file and open with the "OST Viewer"
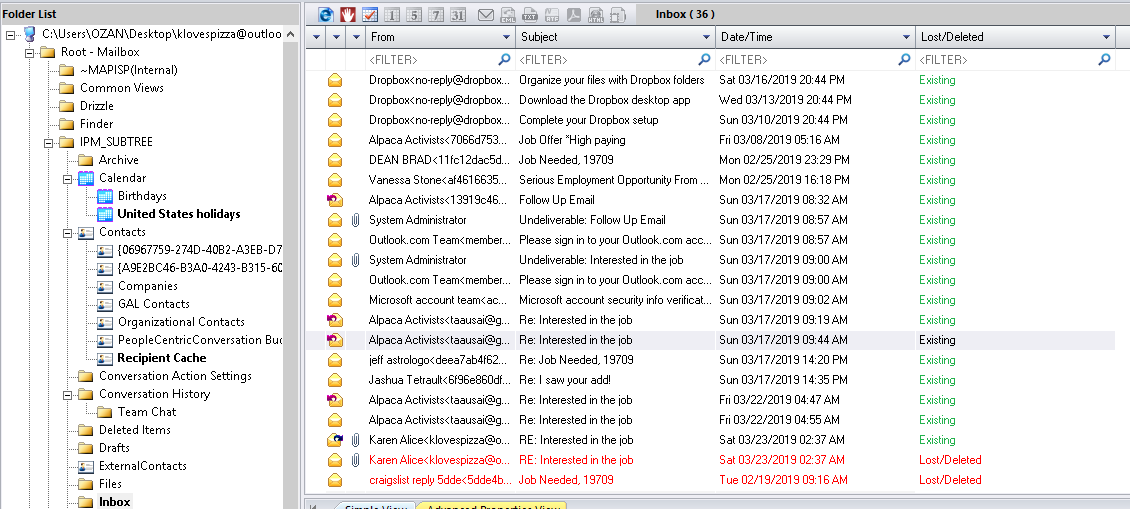
We need the initials of the "Micheal Scotch"
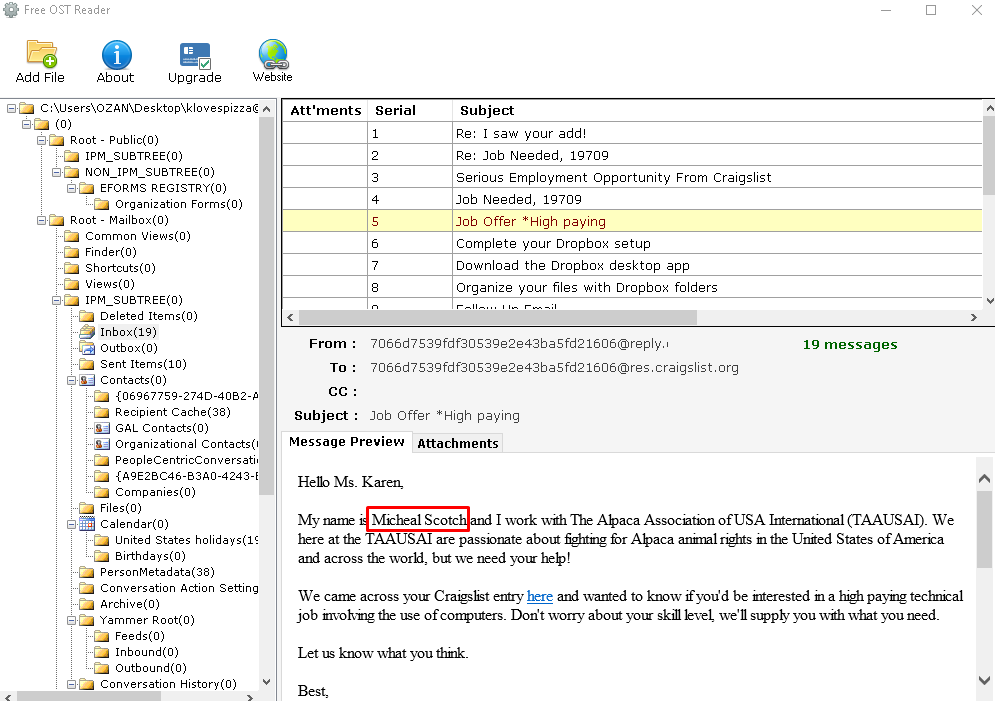
Flag< MS>
13.Make it rain! (15 Point)#
Same with previous question just looking at the e-mails we find the answer.
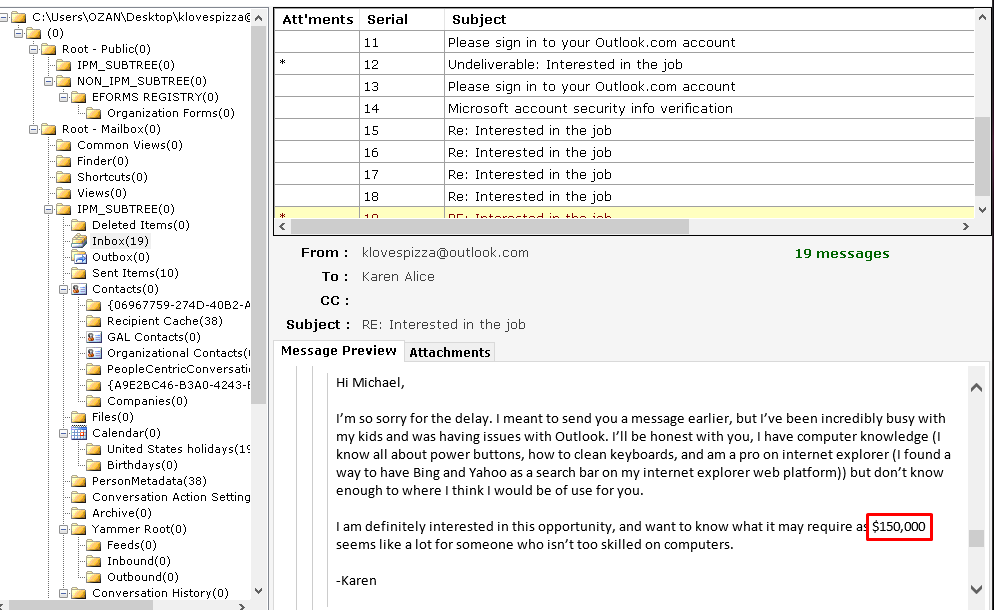
Flag< 150000>
14.You have no idea how high I can fly (15 Point)#
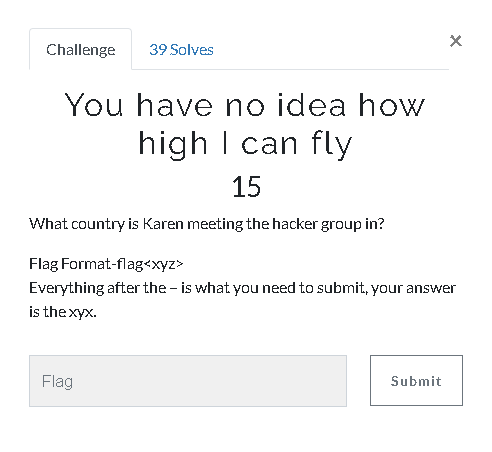
We can see the e-mails with the "Autopsy"
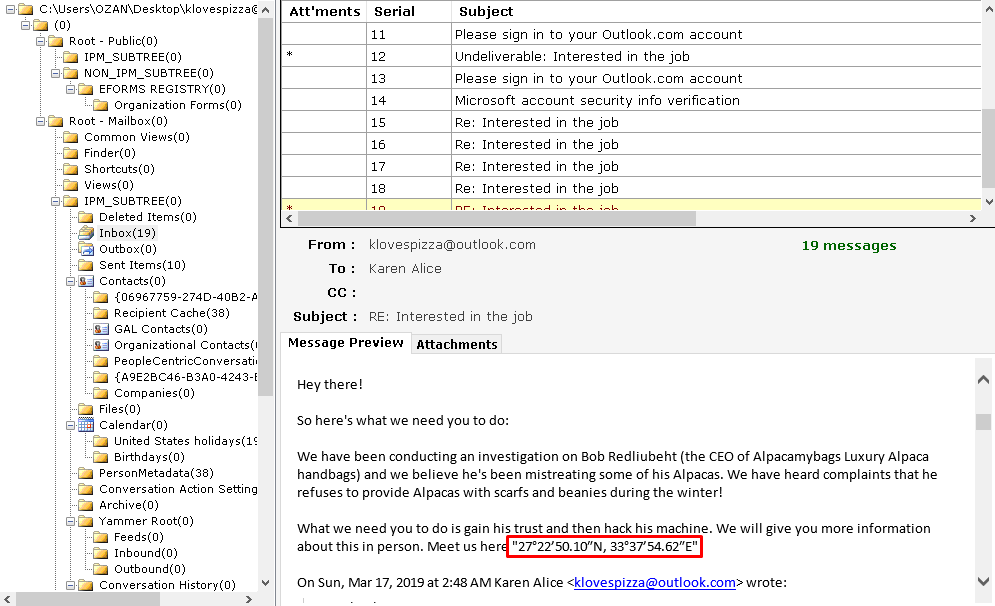
When we search this coordinate on Google Maps we got the answer which is Egypt
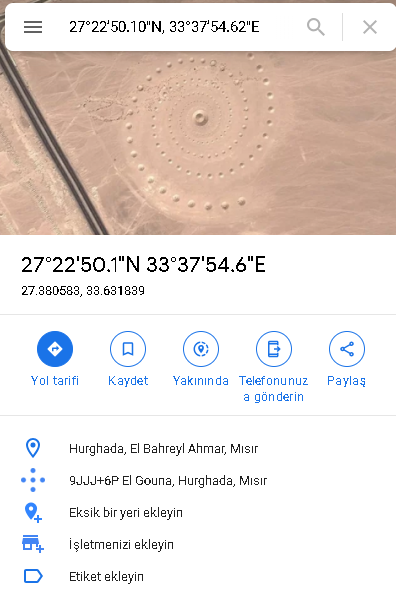
Flag< Egypt>
15.Where in the world is Carmen Sandiego? (15 Point)#
We back to the “SYSTEM” hive and “regripper” again. We can use the “timezone” module.
1
| "rip.exe -r ..\SYSTEM -p timezone"
|
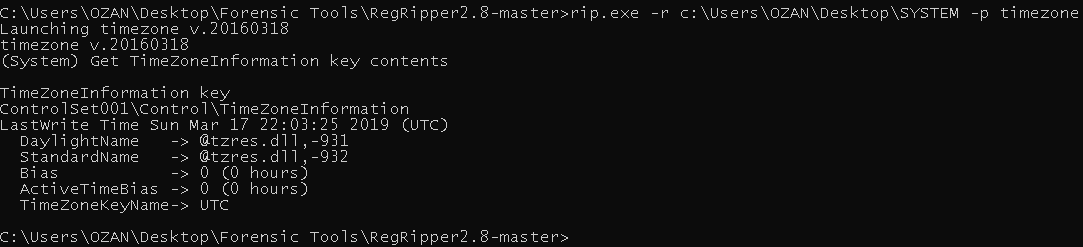
Flag< UTC>
16.Someone actually read that? (15 Point)#
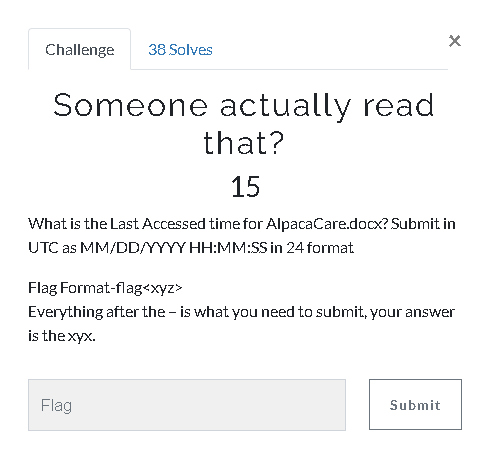
When we go to the “Autopsy\File Types\Documents\Office” we can see “AlpacaCare.docx” file and we can check file metadata.
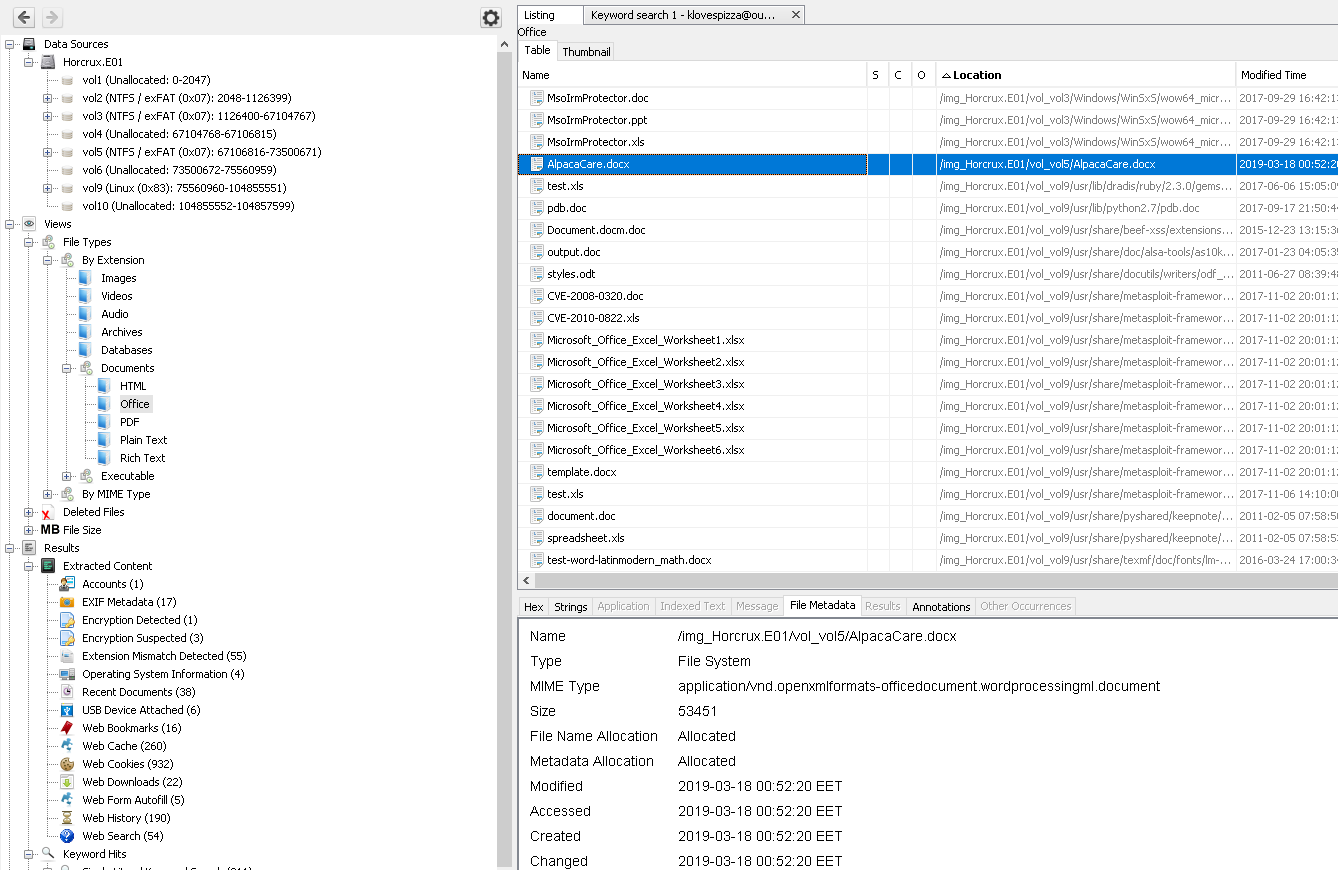
Flag< 03/17/2019 21:52:20>
17.Partition Suspicion (20 Point)#
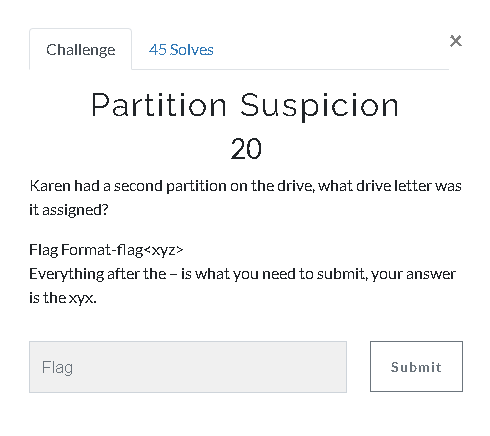
When we check the Recent Documents on Autopsy or manually with C:\Users\Karen\AppData\Roaming\Microsoft\Windows\Recent" we can see a file “PacaLady (A)”
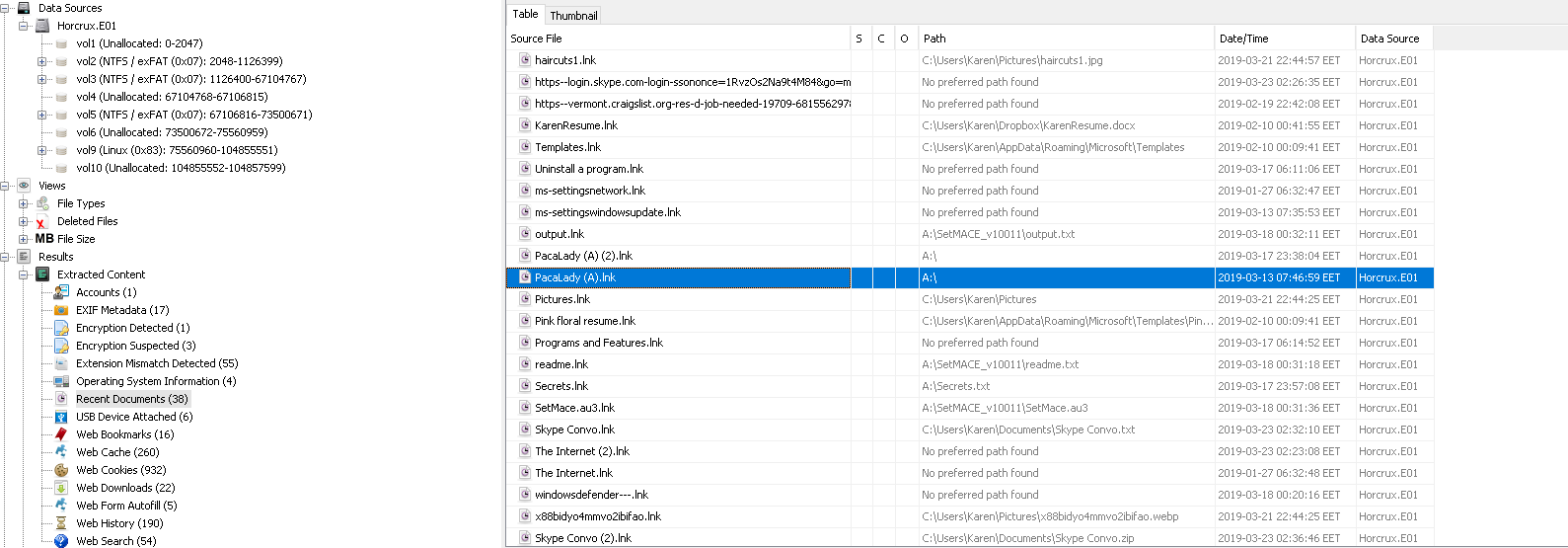
Flag< A>
18.You’ve got questions? I’ve got answers (20 Point)#
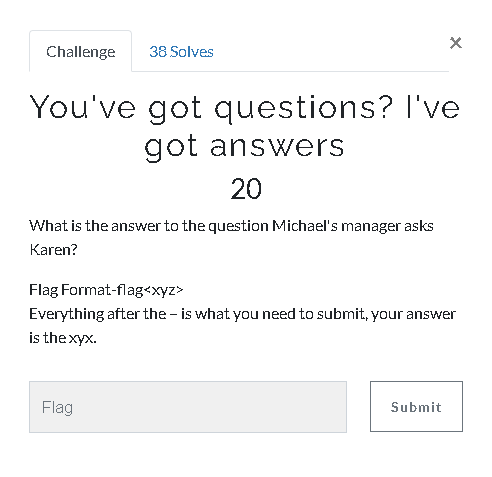
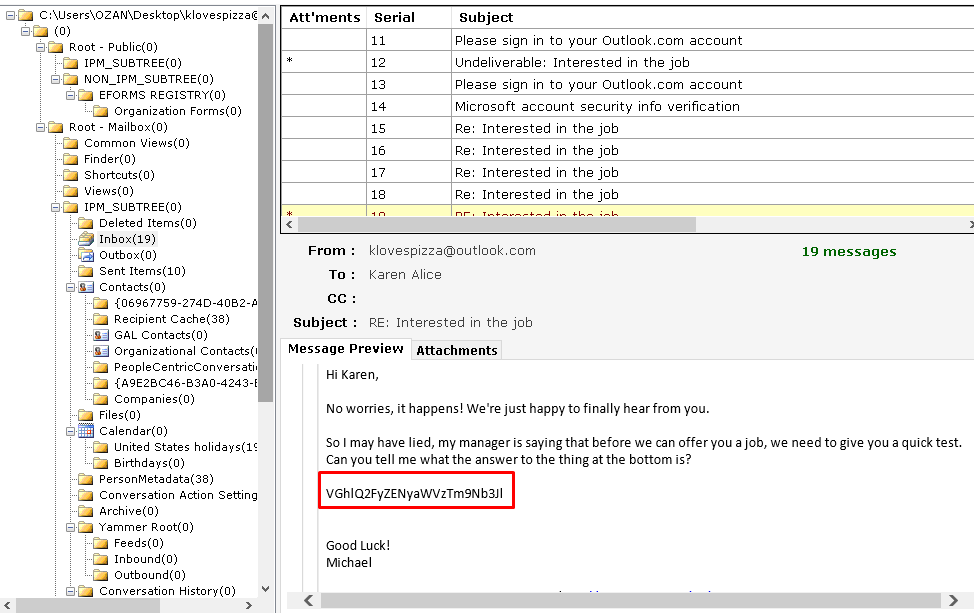
Back to e-mails again. When we looking at Karen's e-mails with Micheal we see a code. We can solve this question just reading the answer of Karen or just decode the text.
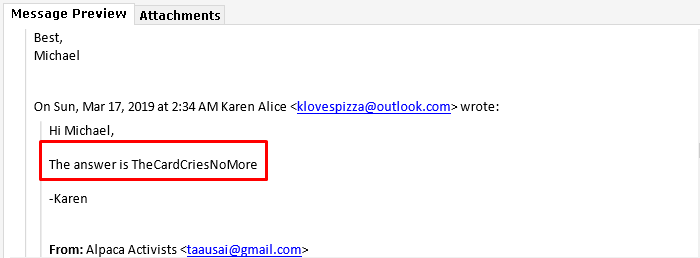
Flag< TheCardCriesNoMore>
19.Recruit Pursuit (20 Point)#
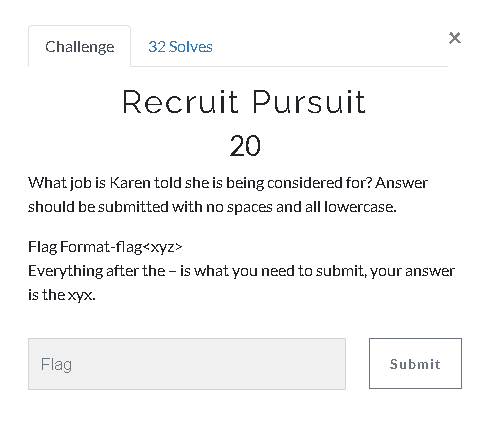
Another e-mail question.
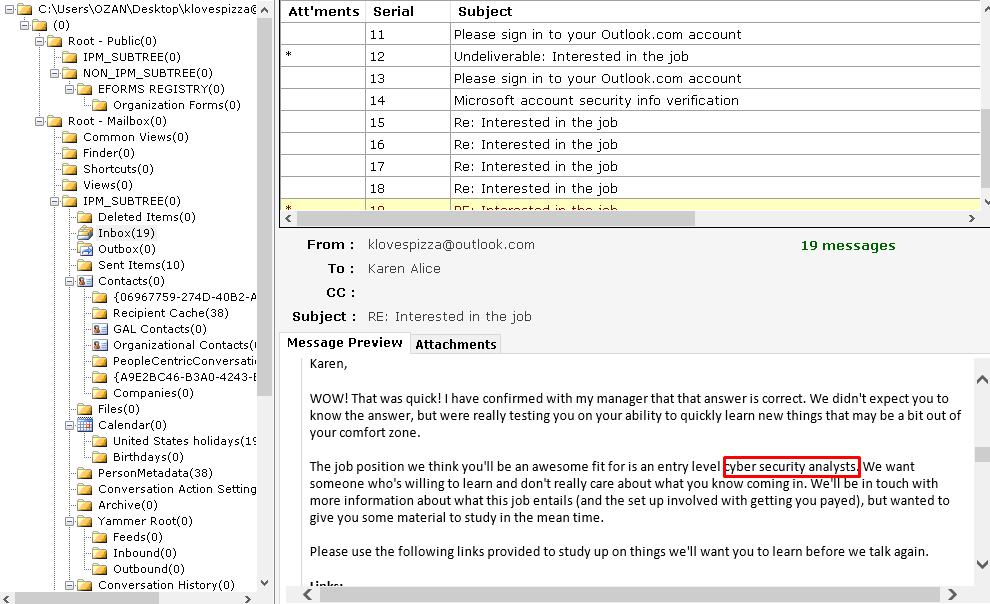
Flag< cybersecurityanalysts>
20.Oh, you’re not supposed to use the same password for everything…? (20 Point)#
We need the “SAM” registry hive to solve this question and parse with regripper.
1
| "rip.exe -r .. \SAM -f sam"
|
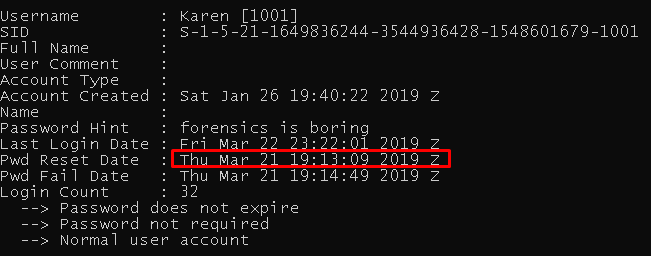
Flag< 03/21/2019 19:13:09>
21.Are you sure you want to change your default browser? (20 Point)#
Under the “C:\Program Files (x86)\Google\Chrome\Application” directory we can see version of Chrome.
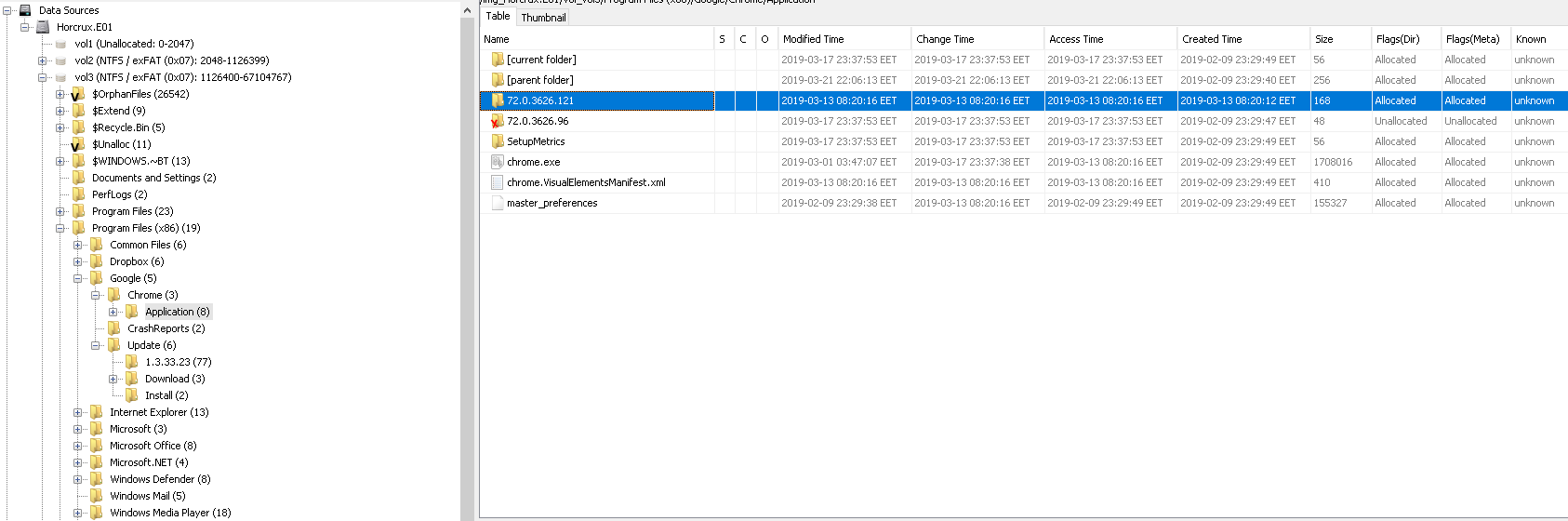
Flag< 72.0.3626.121>
22.iS tHiS sP@M? (22 Point)#
Looking at the e-mails related with “Alpaca” will give us the answer.
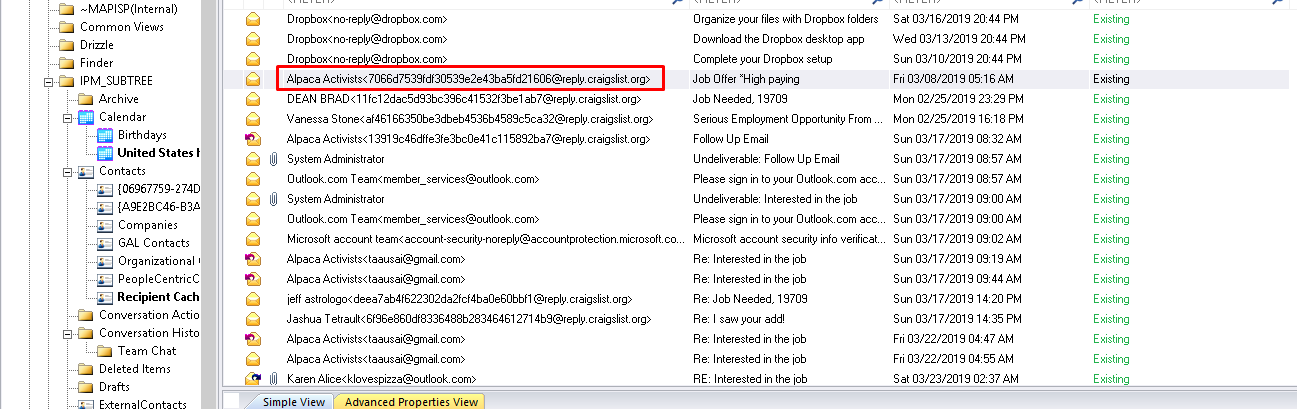
Flag< [email protected]>
23.Moooooooooo (30 Point)#
I've solved this question by chance, I've been examining string values as I browse through the files, and suddenly I'm confronted with the answer, which didn't surprise me.
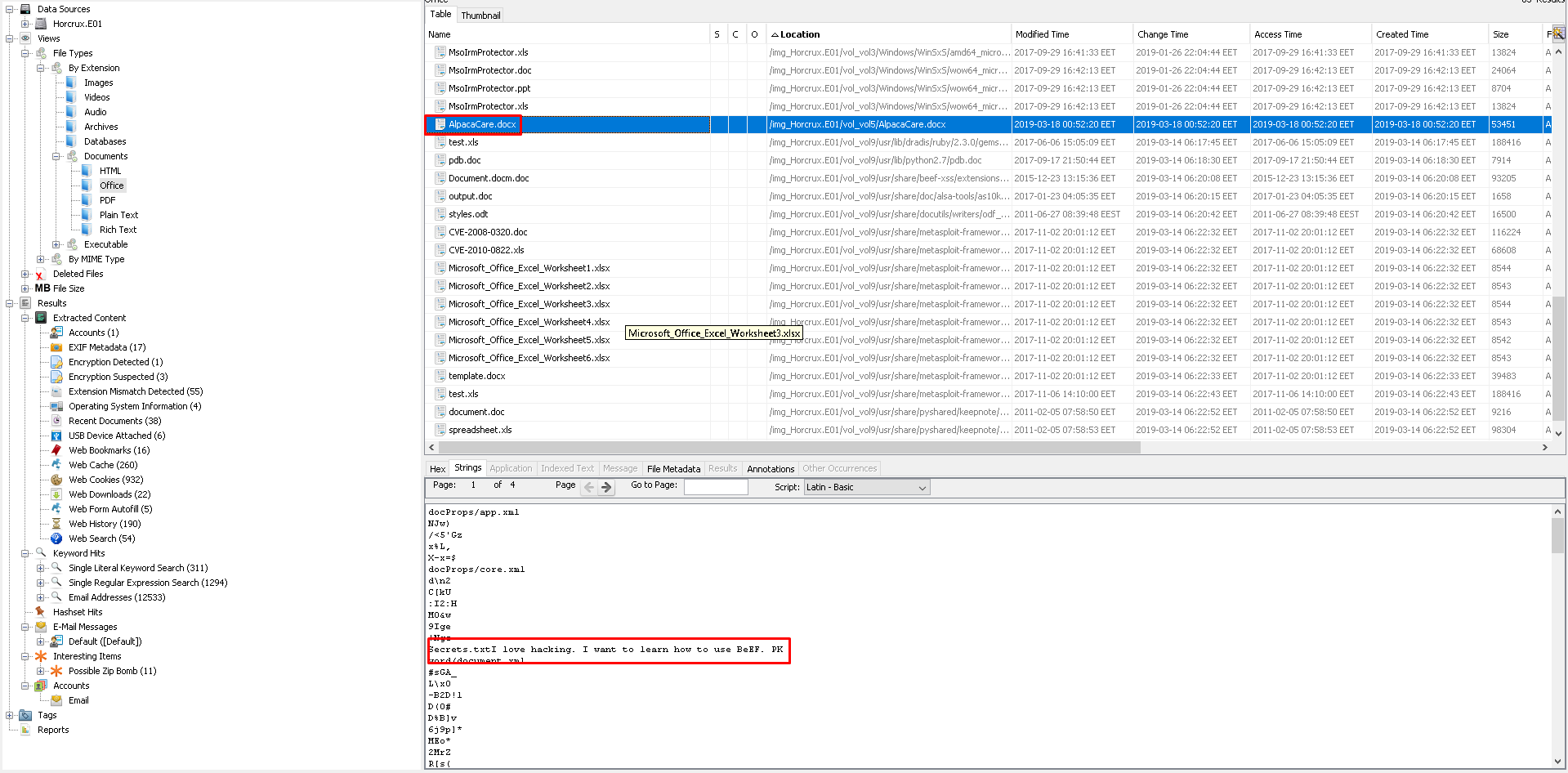
I need understand the title 😊
Flag< BeEF>
24.She’s a ladies man (30 Point)#
Actually we solved this question before at 17th question.
C:\Users\Karen\AppData\Roaming\Microsoft\Windows\Recent"
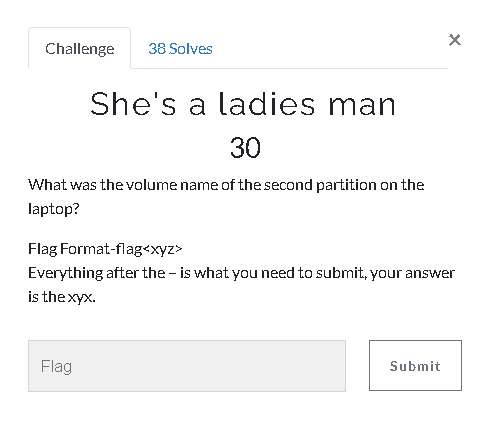
Flag< PacaLady>
25.now with 99% more ads (30 Point)#
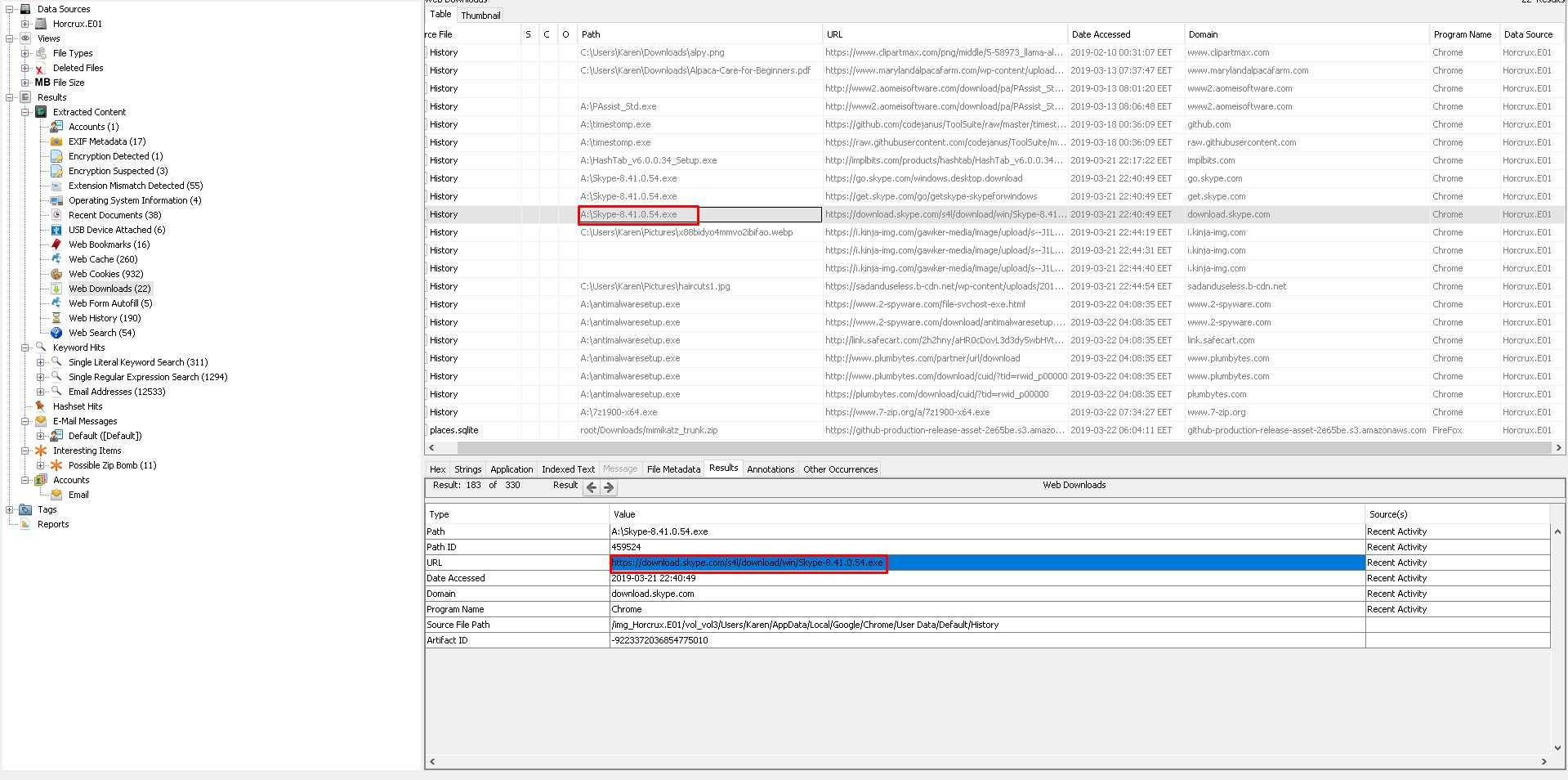
We can look Web Downloads section on Autopsy and detect the URL.
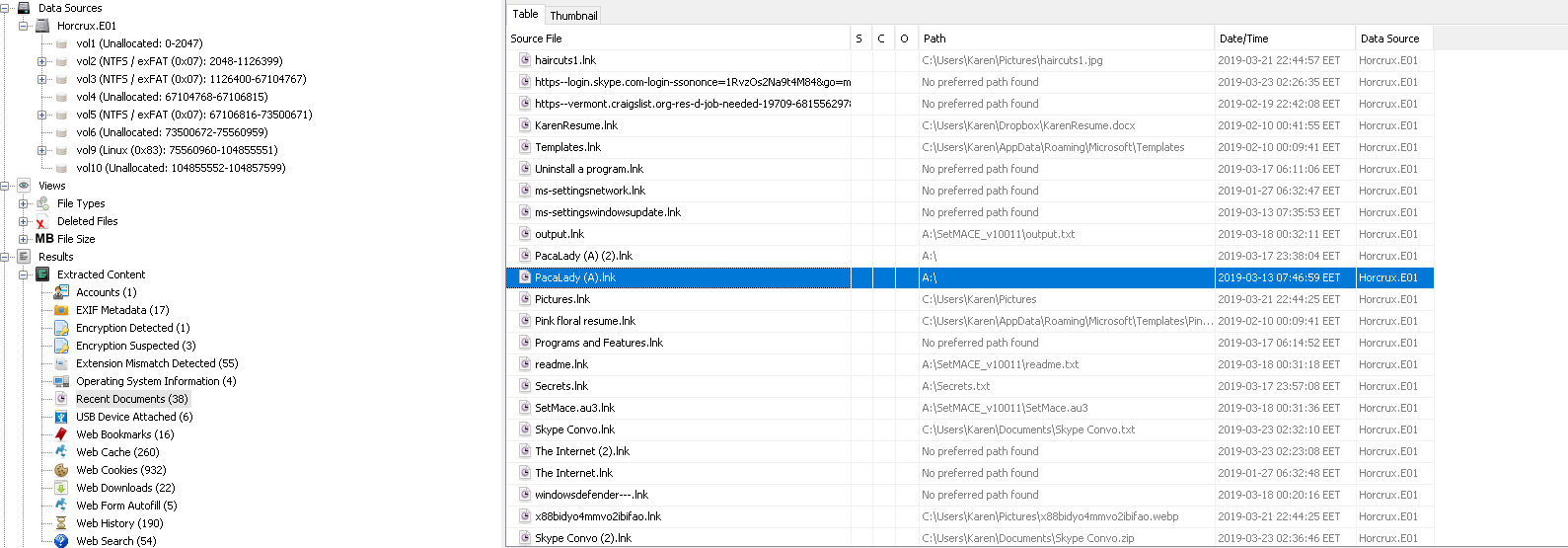
Flag< https://download.skype.com/s4l/download/win/Skype-8.41.0.54.exe>
26.rev2md5 (45 Point)#
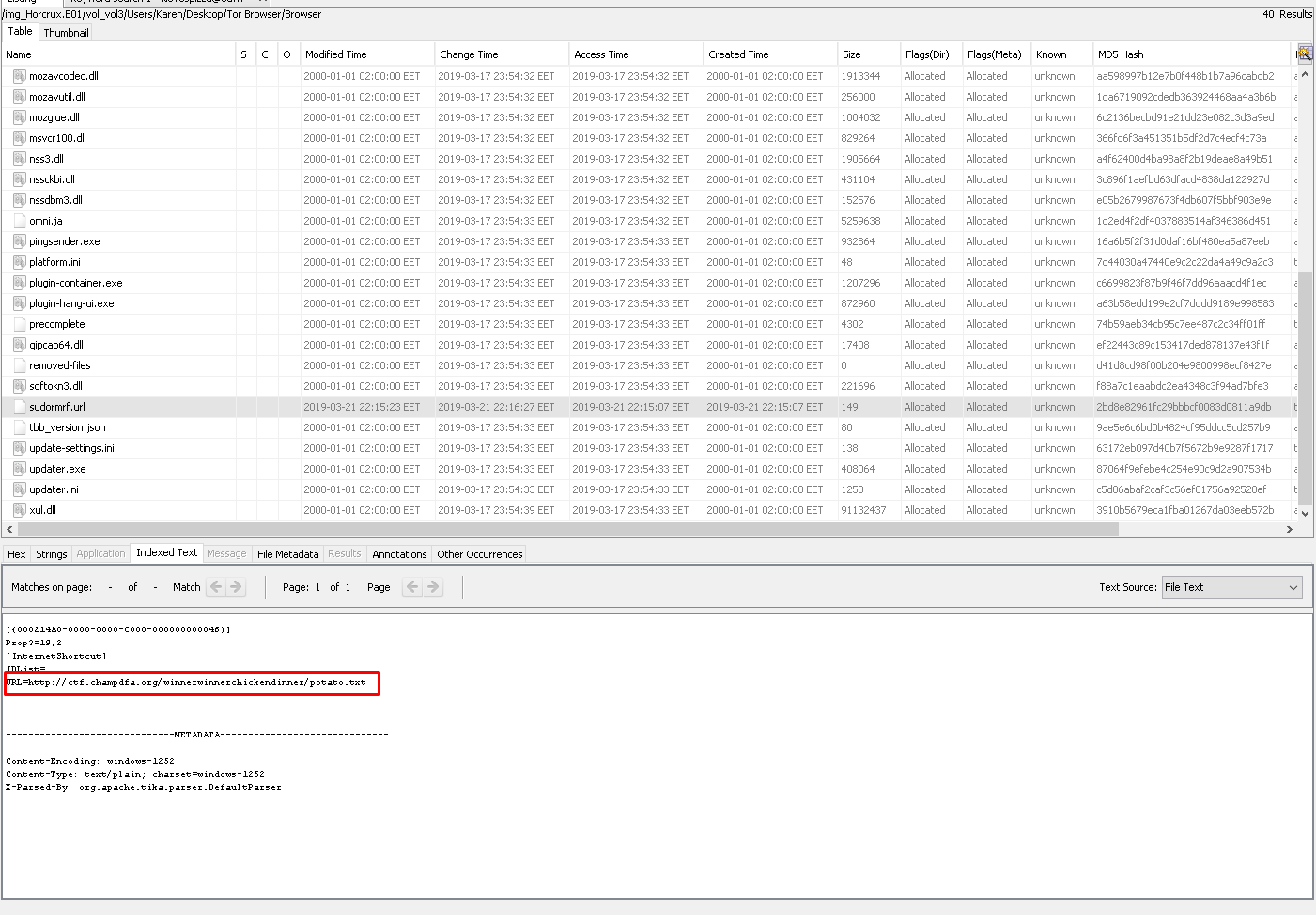
We can use FTK Imager for this question export all the hashes under the "C:\Users" and search the hash that given us.
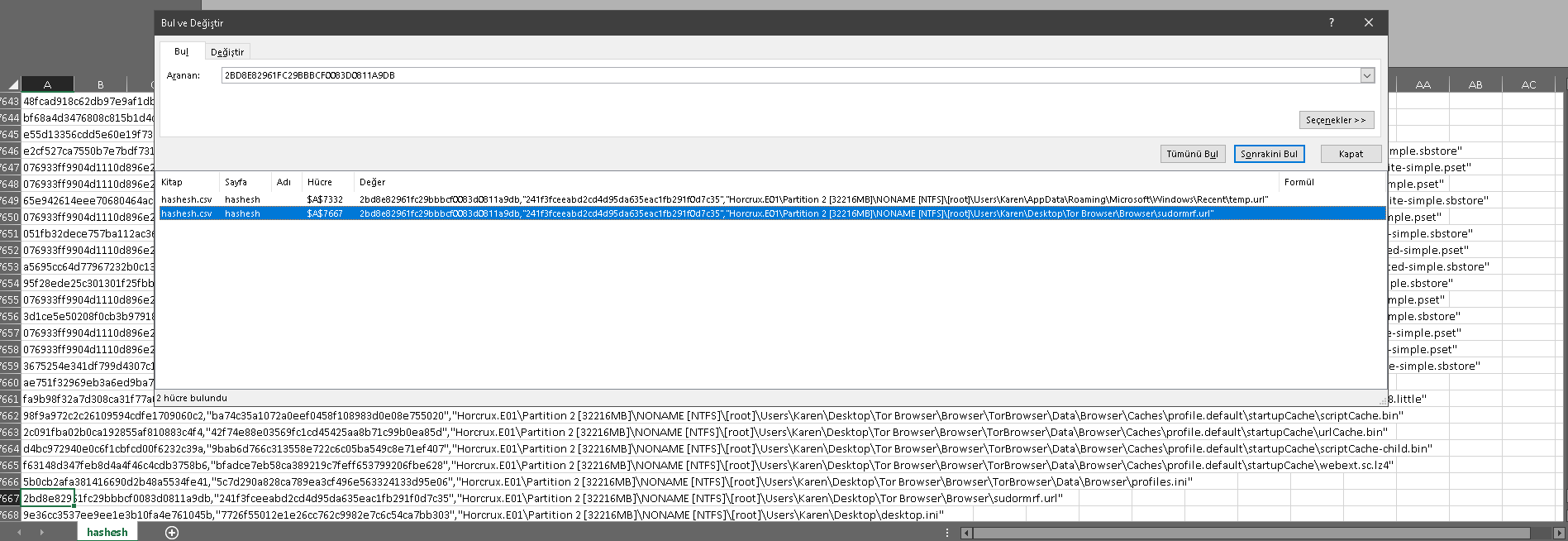
"Users\Karen\Desktop\Tor Browser\Browser\sudormrf.url"
Flag< http://ctf.champdfa.org/winnerwinnerchickendinner/potato.txt>
27.AlpacaCare2020 (75 Point)#
Exporting the AlpcaCare.docx and opening it will give the answer.
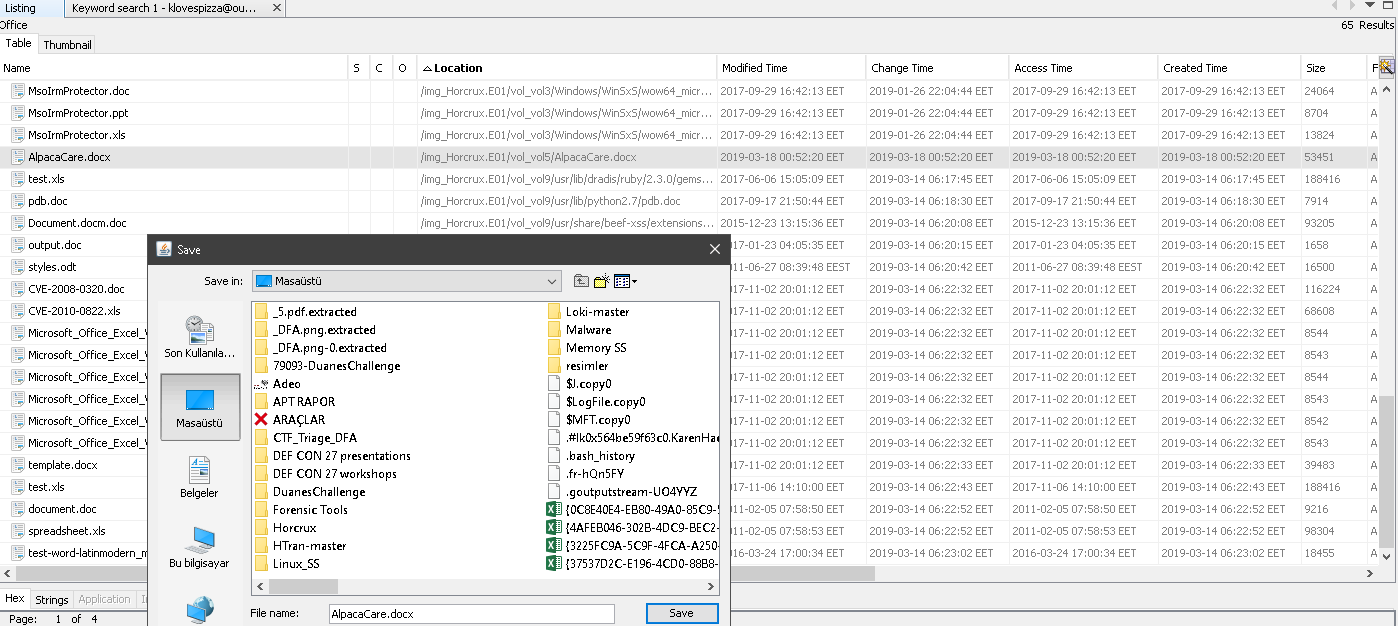
Flag < palominoalpacafarm>
28.You have secrets? (75 Point)#
We need to change the “AlpcaCare.docx” to “AlpcaCare.zip”. When we open the “AlpcaCare.zip” we can see the “Secrets.txt” and when was the file created.
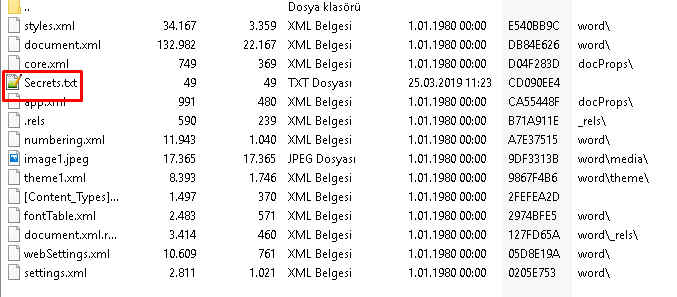
flag < 03/25/2019 08:23:45>
29.DrDD (150 Point)#
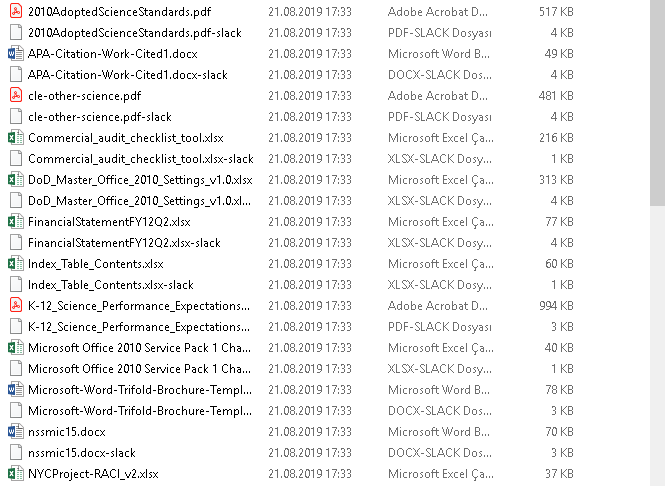
This directory has a lot of junk in it. After checking all files we have a Base64 encoded text in “South_Carolina_Academic_Standards_and_Performance_Indicators_for_Science_2014.pdf”
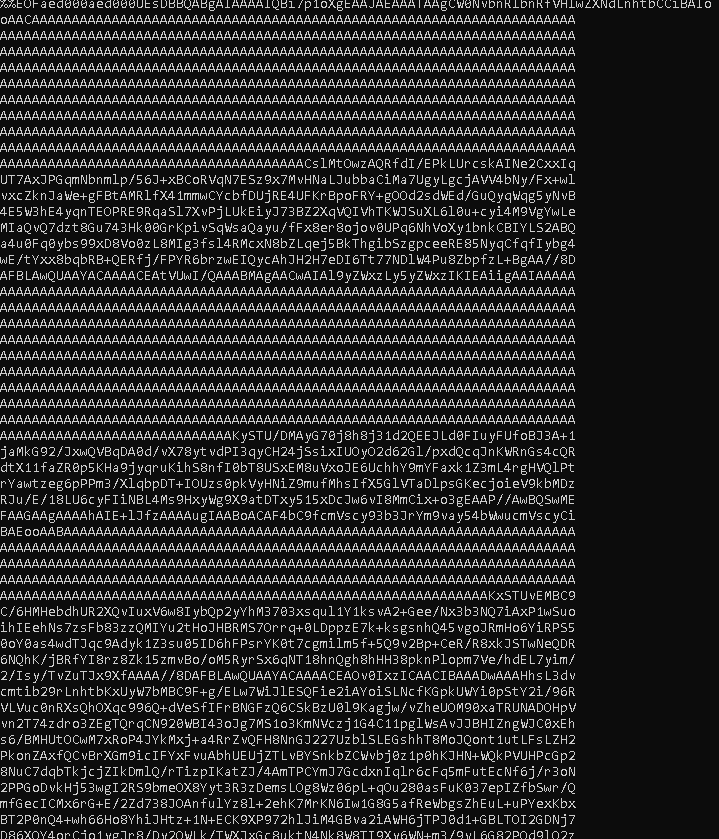
When we encode this text, download and open with excel we got the password of Duane’s Linkedin.
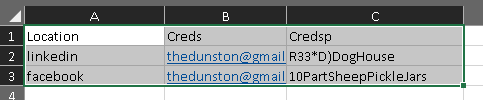
Flag< R33*D)DogHouse>




































































































































































































